F-SECURE ANTI-VIRUS FOR MICROSOFT EXCHANGE 8.00 - Owner's manual
- Category
- Antivirus security software
- Type
- Owner's manual
This manual is also suitable for

F-Secure Client
Security
Administrator’s Guide

"F-Secure" and the triangle symbol are registered trademarks of F-Secure Corporation and F-Secure
product names and symbols/logos are either trademarks or registered trademarks of F-Secure
Corporation. All product names referenced herein are trademarks or registered trademarks of their
respective companies. F-Secure Corporation disclaims proprietary interest in the marks and names of
others. Although F-Secure Corporation makes every effort to ensure that this information is accurate,
F-Secure Corporation will not be liable for any errors or omission of facts contained herein. F-Secure
Corporation reserves the right to modify specifications cited in this document without prior notice.
Companies, names and data used in examples herein are fictitious unless otherwise noted. No part of
this document may be reproduced or transmitted in any form or by any means, electronic or
mechanical, for any purpose, without the express written permission of F-Secure Corporation.
This product may be covered by one or more F-Secure patents, including the following:
Copyright © 2008 F-Secure Corporation. All rights reserved. 12000060-7A10
GB2353372 GB2366691 GB2366692 GB2366693 GB2367933 GB2368233
GB2374260

iii
Contents
About this Guide 10
Overview ............................................................................................................................ 11
Additional Documentation .................................................................................................. 13
Conventions Used in F-Secure Guides.............................................................................. 15
Chapter 1 Introduction 17
1.1 Overview ....................................................................................................................18
1.2 F-Secure Client Security Components and Features................................................. 18
1.2.1 Virus and Spy Protection ................................................................................18
1.2.2 Internet Shield ................................................................................................21
1.2.3 Application Management ................................................................................22
1.3 Introduction to F-Secure Policy Manager...................................................................23
1.3.1 Main Components of F-Secure Policy Manager.............................................24
1.3.2 F-Secure Policy Manager Features................................................................25
1.4 Basic Terminology......................................................................................................26
Chapter 2 Installing F-Secure Policy Manager 28
2.1 Overview ....................................................................................................................29
2.2 System Requirements................................................................................................30
2.2.1 F-Secure Policy Manager Server ...................................................................30
2.2.2 F-Secure Policy Manager Console.................................................................32
2.3 Installation Steps........................................................................................................33
2.4 Uninstalling F-Secure Policy Manager .......................................................................55

iv
Chapter 3 Introduction to F-Secure Policy Manager Anti-Virus Mode
User Interface 56
3.1 Overview ....................................................................................................................57
3.2 Policy Domains Tab ...................................................................................................58
3.3 Management Tabs .....................................................................................................58
3.3.1 Summary Tab .................................................................................................59
3.3.2 Outbreak Tab..................................................................................................66
3.3.3 Settings Tab ................................................................................................... 68
3.3.4 Status Tab ....................................................................................................100
3.3.5 Alerts Tab .....................................................................................................108
3.3.6 Reports Tab..................................................................................................110
3.3.7 Installation Tab .............................................................................................111
3.3.8 Operations Tab.............................................................................................113
3.4 Toolbar .....................................................................................................................114
3.5 Menu Commands.....................................................................................................115
3.6 Settings Inheritance .................................................................................................118
3.6.1 How Settings Inheritance is Displayed on the User Interface.......................120
3.6.2 Locking and Unlocking all Settings on a Page at Once................................121
3.6.3 Settings Inheritance in Tables ......................................................................122
Chapter 4 Setting up the Managed Network 123
4.1 Overview ..................................................................................................................124
4.2 Logging in for the First Time ....................................................................................124
4.2.1 Logging In.....................................................................................................125
4.3 Creating the Domain Structure.................................................................................128
4.3.1 Adding Policy Domains and Subdomains.....................................................130
4.4 Adding Hosts............................................................................................................130
4.4.1 Windows Domains........................................................................................131
4.4.2 Autoregistered Hosts ....................................................................................131
4.4.3 F-Secure Push Installations..........................................................................136
4.4.4 Policy-Based Installation ..............................................................................143
4.4.5 Local Installation and Updates with Pre-Configured Packages....................147
4.5 Local Installation ......................................................................................................152
4.5.1 Local Installation System Requirements ......................................................152

v
4.5.2 Installation Instructions .................................................................................154
4.6 Installing on an Infected Host...................................................................................155
4.7 How to Check That the Management Connections Work ........................................156
Chapter 5 Configuring Virus and Spyware Protection 157
5.1 Overview: What can Virus and Spyware Protection be Used for? ...........................158
5.2 Configuring Automatic Updates ...............................................................................159
5.2.1 How do Automatic Updates Work?...............................................................160
5.2.2 Automatic Updates Configuration Settings...................................................160
5.2.3 Configuring Automatic Updates from Policy Manager Server ......................161
5.2.4 Configuring Policy Manager Proxy ...............................................................162
5.2.5 Configuring Clients to Download Updates from Each Other ........................163
5.3 Configuring Real-Time Scanning .............................................................................164
5.3.1 Real-Time Scanning Configuration Settings.................................................164
5.3.2 Enabling Real-Time Scanning for the Whole Domain ..................................166
5.3.3 Forcing all Hosts to Use Real-Time Scanning..............................................167
5.3.4 Excluding Microsoft Outlooks's .pst File from Real-Time Scanning .............168
5.4 Configuring System Control .....................................................................................169
5.4.1 System Control Configuration Settings.........................................................169
5.4.2 System Control Server Queries (DeepGuard 2.0)........................................170
5.5 Configuring Rootkit Scanning (Blacklight)................................................................170
5.5.1 Rootkit Scanning Configuration Settings ......................................................171
5.5.2 Launching a Rootkit Scan for the Whole Domain.........................................171
5.6 Configuring E-mail Scanning....................................................................................172
5.6.1 E-mail Scanning Configuration Settings .......................................................172
5.6.2 Enabling E-mail Scanning for Incoming and Outgoing E-mails ....................174
5.7 Configuring Web Traffic (HTTP) Scanning...............................................................176
5.7.1 HTTP Scanning Configuration Settings........................................................176
5.7.2 Enabling Web Traffic Scanning for the Whole Domain ................................177
5.7.3 Excluding a Web Site from HTTP Scanning.................................................177
5.8 Configuring Spyware Scanning................................................................................179
5.8.1 Spyware Control Settings .............................................................................179
5.8.2 Setting up Spyware Control for the Whole Domain ......................................183
5.8.3 Launching Spyware Scanning in the Whole Domain....................................185
5.8.4 Allowing the Use of a Spyware or Riskware Component .............................186

vi
5.9 Preventing Users from Changing Settings ...............................................................187
5.9.1 Setting all Virus Protection Settings Final.....................................................187
5.10 Configuring F-Secure Client Security Alert Sending ................................................188
5.10.1 Setting F-Secure Client Security to Send Virus Alerts to an E-mail Address188
5.10.2 Disabling F-Secure Client Security Alert Pop-ups ........................................190
5.11 Monitoring Viruses on the Network ..........................................................................190
5.12 Testing your Antivirus Protection .............................................................................190
Chapter 6 Configuring Internet Shield 192
6.1 Overview: What can Internet Shield be Used for? ...................................................193
6.1.1 Global Firewall Security Levels ....................................................................193
6.1.2 Security Level Design Principles ..................................................................195
6.2 Configuring Internet Shield Security Levels and Rules ............................................196
6.2.1 Selecting an Active Security Level for a Workstation ...................................196
6.2.2 Configuring a Default Security Level for the Managed Hosts.......................197
6.2.3 Adding a New Security Level for a Certain Domain Only .............................198
6.3 Configuring Network Quarantine..............................................................................201
6.3.1 Network Quarantine Settings........................................................................201
6.3.2 Enabling Network Quarantine in the Whole Domain ....................................201
6.3.3 Fine-Tuning Network Quarantine .................................................................202
6.4 Configuring Internet Shield Rule Alerts ....................................................................203
6.4.1 Adding a New Internet Shield Rule with Alerting ..........................................203
6.5 Configuring Application Control................................................................................207
6.5.1 Application Control Configuration Settings ...................................................209
6.5.2 Setting up Application Control for the First Time ..........................................210
6.5.3 Creating a Rule for an Unknown Application on Root Level.........................212
6.5.4 Editing an Existing Application Control Rule ................................................213
6.5.5 Disabling Application Control Pop-ups .........................................................214
6.6 How to use Alerts for Checking that Internet Shield Works? ...................................215
6.7 Configuring the Intrusion Prevention........................................................................216
6.7.1 Intrusion Prevention Configuration Settings .................................................217
6.7.2 Configuring IPS for Desktops and Laptops ..................................................218
Chapter 7 How to Check that the Environment is Protected 220
7.1 Overview ..................................................................................................................221

vii
7.2 How to Check the Protection Status from Outbreak Tab .........................................221
7.3 How to Check that all the Hosts Have the Latest Policy ..........................................221
7.4 How to Check that the Server has the Latest Virus Definitions................................222
7.5 How to Check that the Hosts have the Latest Virus Definitions ...............................222
7.6 How to Check that there are no Disconnected Hosts ..............................................223
7.7 Viewing Scanning Reports .......................................................................................223
7.8 Viewing Alerts ..........................................................................................................224
7.9 Creating a Weekly Infection Report .........................................................................225
7.10 Monitoring a Possible Network Attack......................................................................225
Chapter 8 Upgrading Software 227
8.1 Overview: Upgrading Software ................................................................................228
8.1.1 Using the Installation Editor..........................................................................228
Chapter 9 Local Host Operations 232
9.1 Overview ..................................................................................................................233
9.2 Scanning File Viruses Manually ...............................................................................233
9.3 Viewing the Latest Scanning Report on a Local Host ..............................................234
9.4 Adding a Scheduled Scan from a Local Host...........................................................234
9.5 Logging and Log File Locations on Local Hosts ......................................................235
9.5.1 The LogFile.log file .......................................................................................235
9.5.2 Packet Logging.............................................................................................236
9.5.3 The Action.log file .........................................................................................237
9.5.4 Other Log Files .............................................................................................239
9.6 Connecting to F-Secure Policy Manager and Importing a Policy File Manually.......239
9.7 Suspending Downloads and Updates ......................................................................240
9.8 Allowing Users to Unload F-Secure Products ..........................................................240
Chapter 10 Virus Information 242
10.1 Malware Information and Tools on the F-Secure Web Pages .................................243
10.2 How to Send a Virus Sample to F-Secure ...............................................................244
10.2.1 How to Package a Virus Sample ..................................................................244
10.2.2 What Should Be Sent ...................................................................................244

viii
10.2.3 How to Send the Virus Sample.....................................................................247
10.2.4 In What Language ........................................................................................247
10.2.5 Response Times...........................................................................................247
10.3 What to Do in Case of a Virus Outbreak? ................................................................248
Chapter 11 Setting Up the Cisco NAC Plugin 250
11.1 Introduction ..............................................................................................................251
11.2 Installing the Cisco NAC Plugin ...............................................................................251
11.2.1 Importing Posture Validation Attribute Definitions ........................................252
11.3 Attributes to be Used for Application Posture Token ...............................................252
Chapter 12 Advanced Features: Virus and Spyware Protection 254
12.1 Overview ..................................................................................................................255
12.2 Configuring Scheduled Scanning.............................................................................255
12.3 Advanced System Control Settings..........................................................................257
12.3.1 Notify User on a Deny Event ........................................................................257
12.3.2 Let an Administrator Allow or Deny Events from Other Users Programs .....258
12.3.3 Automatically Allow or Deny Events Requested by a Specific Application...258
12.4 Configuring Policy Manager Proxy...........................................................................260
12.5 Configuring Automatic Updates on Hosts from Policy Manager Proxy ....................260
12.6 Configuring a Host for SNMP Management.............................................................261
12.7 Excluding an Application from the Web Traffic Scanner ..........................................262
Chapter 13 Advanced Features: Internet Shield 263
13.1 Overview ..................................................................................................................264
13.2 Managing Internet Shield Properties Remotely........................................................264
13.2.1 Packet Logging.............................................................................................264
13.2.2 Trusted Interface ..........................................................................................265
13.2.3 Packet Filtering.............................................................................................266
13.3 Configuring Security Level Autoselection.................................................................266
13.4 Troubleshooting Connection Problems ....................................................................268
13.5 Adding New Services ...............................................................................................269
13.5.1 Creating a New Internet Service based on the Default HTTP ......................270
13.6 Setting up Dialup Control .........................................................................................278

ix
13.6.1 Allowing and Blocking Phone Numbers........................................................278
13.6.2 Call Logging..................................................................................................279
Appendix A Modifying PRODSETT.INI 281
A.1 Overview ................................................................................................................. 282
A.2 Configurable Prodsett.ini Settings............................................................................282
Appendix B E-mail Scanning Alert and Error Messages 294
B.1 Overview ................................................................................................................. 295
Appendix C Products Detected or Removed During Client Installation 299
C.1 Overview ................................................................................................................. 300
Glossary 306
Technical Support 320
Overview .......................................................................................................................... 321
Web Club .........................................................................................................................321
Advanced Technical Support ...........................................................................................321
F-Secure Technical Product Training ...............................................................................322

10
ABOUT THIS GUIDE
Overview..................................................................................... 11
Additional Documentation.......................................................... 13

11
Overview
This manual covers the configuration and operations that you can do with
the F-Secure Policy Manager Anti-Virus Mode user interface and provides
the information you need to get started with managing F-Secure Client
Security applications centrally.
The F-Secure Client Security Administrator’s Guide is divided into the
following chapters.
Chapter 1. Introduction. Describes the basic components of F-Secure
Client Security and the main features of F-Secure Policy Manager.
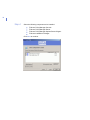
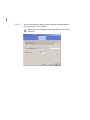
Chapter 2. Installing F-Secure Policy Manager. Instructions on how to
install F-Secure Policy Manager Server and Console.
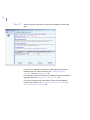
Chapter 3. Introduction to F-Secure Policy Manager Anti-Virus Mode
User Interface. Describes the F-Secure Policy Manager Anti-Virus Mode
user interface components.
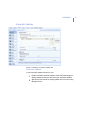
Chapter 4. Setting up the Managed Network. Describes how to plan and
create the centrally managed network.
Chapter 5. Configuring Virus and Spyware Protection. Describes how to
configure Virus Definition Updates, Real-Time Scanning and E-Mail
Scanning.
Chapter 6. Configuring Internet Shield. Describes how to configure the
security levels and rules, Application Control and Intrusion Prevention
System (IPS).
Chapter 7. How to Check that the Environment is Protected. Provides a
checklist for monitoring the domain and for making sure that the network
is protected.
Chapter 8. Upgrading Software. Contains instructions on how to upgrade
software with F-Secure Policy Manager.
Chapter 9. Local Host Operations. Provides information on
administration tasks, such as scheduling a scan locally and collecting
information from local log files.

12
Chapter 10. Virus Information. Describes where you can get more
information about viruses and how you can send a virus sample to
F-Secure.
Chapter 11. Setting Up the Cisco NAC Plugin. Describes how to install
and set up Cisco network Access Control (NAC) Support.
Chapter 12. Advanced Features: Virus and Spyware Protection. Covers
the advanced virus protection features, such as scheduled scanning, the
use of Anti-Virus Proxy and using SNMP-based management.
Chapter 13. Advanced Features: Internet Shield. Covers the advanced
Internet Shield features, such as using port and IP checking with
Application Control, adding new services and troubleshooting connection
problems.
Appendix A. Modifying PRODSETT.INI. Contains information about
modifying PRODSETT.INI, a file that informs the Setup program which
software modules to install on workstations.
Appendix B. E-mail Scanning Alert and Error Messages. Describes the
alert and error messages that E-mail Scanning can generate.
Appendix C. Products Detected or Removed During Client Installation.
Lists all the products that the user is prompted to uninstall or are
uninstalled automatically during F-Secure Client Security installation.
Glossary — Explanation of terms
Technical Support — Web Club and contact information for assistance.
About F-Secure Corporation — Company background and products.

13
Additional Documentation
F-Secure Policy Manager Online Help
The F-Secure Policy Manager Online Help contains information on both
the Anti-Virus Mode as well as the Advanced Mode user interfaces. The
online help is accessible from the Help menu by selecting Help Contents,
or by pressing F1.
Information concerning the F-Secure Policy Manager Anti-Virus Mode
user interface can be found under F-Secure Client Security
Administration in the navigation tree.
Information concerning F-Secure Policy Manager Advanced Mode user
interface and other advanced operations can be found under F-Secure
Policy Manager in the navigation tree.
F-Secure Client Security Online Help
The F-Secure Client Security local user interface comes with a
context-sensitive online help. The online help is accessible from the main
user interface and from the advanced dialogs by either clicking the Help
button or pressing F1.
The online help always opens to a page that holds information about your
current location in the F-Secure Client Security user interface. In the left
pane of the online help, you can browse through the help using the
contents tree and access a full search function.

14
F-Secure Policy Manager Administrator’s Guide
For more information on administering other F-Secure software products
with F-Secure Policy Manager, see F-Secure Policy Manager
Administrator’s Guide. It contains information on the Advanced Mode
user interface and instructions on how you can configure and manage
other F-Secure products. It also includes information on F-Secure
Management Agent, F-Secure Policy Manager Web Reporting.
F-Secure Policy Manager Proxy Administrator’s Guide
For more information on installing and maintaining F-Secure Policy
Manager Proxies, see the F-Secure Policy Manager Proxy
Administrator’s guide. It contains detailed instructions on how you can
use F-Secure Policy Manager Proxies to more efficiently deliver product
updates.

15
Conventions Used in F-Secure Guides
This section describes the symbols, fonts, and terminology used in this
manual.
Symbols
⇒ An arrow indicates a one-step procedure.
Fonts
Arial bold (blue) is used to refer to menu names and commands, to
buttons and other items in a dialog box.
Arial Italics (blue) is used to refer to other chapters in the manual, book
titles, and titles of other manuals.
Arial Italics (black) is used for file and folder names, for figure and table
captions, and for directory tree names.
Courier New is used for messages on your computer screen.
WARNING: The warning symbol indicates a situation with a
risk of irreversible destruction to data.
IMPORTANT: An exclamation mark provides important information
that you need to consider.
REFERENCE - A book refers you to related information on the
topic available in another document.
l
NOTE - A note provides additional information that you should
consider.
TIP - A tip provides information that can help you perform a task
more quickly or easily.

16
Courier New bold is used for information that you must type.
SMALL CAPS (BLACK) is used for a key or key combination on your
keyboard.
Arial underlined (blue)
is used for user interface links.
Arial italics is used for window and dialog box names.
PDF Document
This manual is provided in PDF (Portable Document Format). The PDF
document can be used for online viewing and printing using Adobe®
Acrobat® Reader. When printing the manual, please print the entire
manual, including the copyright and disclaimer statements.
For More Information
Visit F-Secure at http://www.f-secure.com for documentation, training
courses, downloads, and service and support contacts.
In our constant attempts to improve our documentation, we would
welcome your feedback. If you have any questions, comments, or
suggestions about this or any other F-Secure document, please contact
us at documentation@f-secure.com
.

17
1
INTRODUCTION
Overview..................................................................................... 18
F-Secure Client Security Components and Features................. 18
Introduction to F-Secure Policy Manager ................................... 23
Basic Terminology ...................................................................... 26

18
1.1 Overview
This section describes the main components of F-Secure Client Security
and F-Secure Policy Manager and provides an introduction to policy
based management.
1.2 F-Secure Client Security Components and
Features
F-Secure Client Security is used for protecting the computer against
viruses, worms, spyware, rootkits and other malware, and against
unauthorized access from the network. F-Secure Client Security consists
of Virus Protection, Internet Shield, and Application Management. When
installing F-Secure Client Security, you can select which of these
components are installed.
1.2.1 Virus and Spy Protection
Virus and Spy Protection includes several scanning methods: Real-Time
Scanning, E-mail Scanning, Web Traffic Scanning, Rootkit Scanning, and
Manual Scanning. It also includes System Control, Automatic Updates,
the F-Secure Automatic Update Agent and the Virus News service.
Real-Time Scanning
The Real-Time Scanning feature gives you continuous protection against
viruses and spyware as files are opened, copied, moved, renamed and
downloaded from the Web.
Real-Time Scanning functions transparently in the background, looking
for viruses whenever you access files on the hard disk, diskettes, or
network drives. If you try to access an infected file, Real-Time Scanning
will automatically stop the virus from executing. It will then either remove it
from the file or display a warning, as specified in the security policy. For
more information, see “Configuring Real-Time Scanning”, 164.

CHAPTER 1 19
E-mail Scanning
E-mail Scanning can be used for scanning both incoming and outgoing
e-mail messages and attachments. It prevents viruses from getting inside
the company network and it also prevents you from accidentally sending
infected attachments outside. E-mail Scanning can be configured to drop
infected attachments from incoming e-mails. When it has found an
infection in an outgoing e-mail, it can block the outgoing e-mail traffic until
the problem has been solved. For more information, see “Configuring
E-mail Scanning”, 172.
Web Traffic (HTTP) Scanning
Web Traffic Scanning protects computers against viruses in HTTP traffic.
It scans HTML files, image files, downloaded applications and executable
files, and removes viruses automatically. For more information, see
“Configuring Web Traffic (HTTP) Scanning”, 176.
Rootkit Scanning
If you want to ensure there are no suspicious hidden files, hidden
processes, hidden applications or hidden drives in your computer, you
can scan the system manually for rootkits. For more information, see
“Configuring Rootkit Scanning (Blacklight)”, 170.
Manual Scanning
You can use Manual Scanning, for example, after you have installed
F-Secure Client Security, if you suspect that there might be a virus or
spyware on the computer, or if a virus has been found in the local area
network. You can select whether all files or only a certain types of files are
scanned. You can also decide what action to take with an infected file, the
Disinfection Wizard will guide you through the process. You can also use
the Scheduled Scanning feature to scan your computer automatically
and regularly, for example weekly or 1-2 times a month.

20
System Control
System Control is a new, host-based intrusion prevention system that
analyzes the behavior of files and programs. It provides an extra-layer of
protection by blocking undiscovered viruses, worms, and other malicious
code that try to perform harmful actions on your computer. For more
information, see “Configuring System Control”, 169.
Automatic Updates
The Automatic Updates feature keeps the virus and spyware definitions
always up-to-date. The virus definitions updates are signed by F-Secure
Anti-Virus Research Team. The signature is based on strong encryption
and the packet cannot be altered in transit.
In case of complex viruses the virus definitions updates include removal
tools that are executable binaries. The integrity of the delivered
executable code is very important, and F-Secure scanning engines check
that all update code is signed by F-Secure Anti-Virus Research. If the
integrity is compromised, the code will not be executed. For more
information, see “Configuring Automatic Updates”, 159.
F-Secure Automatic Update Agent
With F-Secure Automatic Update Agent, you are able to receive virus
definition updates and informational content without interrupting your
work to wait for files to download from the Web. F-Secure Automatic
Update Agent downloads files automatically in the background using
bandwidth not being used by other Internet applications, so you can
always be sure they will have the latest updates without having to search
the Web.
If the F-Secure Automatic Update Agent is always connected to the
Internet, it will automatically receive new virus definition updates after
they have been published by F-Secure.
When the F-Secure Automatic Update Agent service is started, it
connects to F-Secure’s Automatic Update Server. The agent will keep
polling the server regularly to see whether there is new content available.
The agent downloads only the parts of virus definitions that have changed
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
-
 1
1
-
 2
2
-
 3
3
-
 4
4
-
 5
5
-
 6
6
-
 7
7
-
 8
8
-
 9
9
-
 10
10
-
 11
11
-
 12
12
-
 13
13
-
 14
14
-
 15
15
-
 16
16
-
 17
17
-
 18
18
-
 19
19
-
 20
20
-
 21
21
-
 22
22
-
 23
23
-
 24
24
-
 25
25
-
 26
26
-
 27
27
-
 28
28
-
 29
29
-
 30
30
-
 31
31
-
 32
32
-
 33
33
-
 34
34
-
 35
35
-
 36
36
-
 37
37
-
 38
38
-
 39
39
-
 40
40
-
 41
41
-
 42
42
-
 43
43
-
 44
44
-
 45
45
-
 46
46
-
 47
47
-
 48
48
-
 49
49
-
 50
50
-
 51
51
-
 52
52
-
 53
53
-
 54
54
-
 55
55
-
 56
56
-
 57
57
-
 58
58
-
 59
59
-
 60
60
-
 61
61
-
 62
62
-
 63
63
-
 64
64
-
 65
65
-
 66
66
-
 67
67
-
 68
68
-
 69
69
-
 70
70
-
 71
71
-
 72
72
-
 73
73
-
 74
74
-
 75
75
-
 76
76
-
 77
77
-
 78
78
-
 79
79
-
 80
80
-
 81
81
-
 82
82
-
 83
83
-
 84
84
-
 85
85
-
 86
86
-
 87
87
-
 88
88
-
 89
89
-
 90
90
-
 91
91
-
 92
92
-
 93
93
-
 94
94
-
 95
95
-
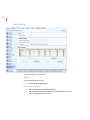 96
96
-
 97
97
-
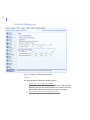 98
98
-
 99
99
-
 100
100
-
 101
101
-
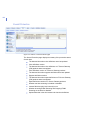 102
102
-
 103
103
-
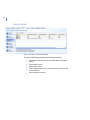 104
104
-
 105
105
-
 106
106
-
 107
107
-
 108
108
-
 109
109
-
 110
110
-
 111
111
-
 112
112
-
 113
113
-
 114
114
-
 115
115
-
 116
116
-
 117
117
-
 118
118
-
 119
119
-
 120
120
-
 121
121
-
 122
122
-
 123
123
-
 124
124
-
 125
125
-
 126
126
-
 127
127
-
 128
128
-
 129
129
-
 130
130
-
 131
131
-
 132
132
-
 133
133
-
 134
134
-
 135
135
-
 136
136
-
 137
137
-
 138
138
-
 139
139
-
 140
140
-
 141
141
-
 142
142
-
 143
143
-
 144
144
-
 145
145
-
 146
146
-
 147
147
-
 148
148
-
 149
149
-
 150
150
-
 151
151
-
 152
152
-
 153
153
-
 154
154
-
 155
155
-
 156
156
-
 157
157
-
 158
158
-
 159
159
-
 160
160
-
 161
161
-
 162
162
-
 163
163
-
 164
164
-
 165
165
-
 166
166
-
 167
167
-
 168
168
-
 169
169
-
 170
170
-
 171
171
-
 172
172
-
 173
173
-
 174
174
-
 175
175
-
 176
176
-
 177
177
-
 178
178
-
 179
179
-
 180
180
-
 181
181
-
 182
182
-
 183
183
-
 184
184
-
 185
185
-
 186
186
-
 187
187
-
 188
188
-
 189
189
-
 190
190
-
 191
191
-
 192
192
-
 193
193
-
 194
194
-
 195
195
-
 196
196
-
 197
197
-
 198
198
-
 199
199
-
 200
200
-
 201
201
-
 202
202
-
 203
203
-
 204
204
-
 205
205
-
 206
206
-
 207
207
-
 208
208
-
 209
209
-
 210
210
-
 211
211
-
 212
212
-
 213
213
-
 214
214
-
 215
215
-
 216
216
-
 217
217
-
 218
218
-
 219
219
-
 220
220
-
 221
221
-
 222
222
-
 223
223
-
 224
224
-
 225
225
-
 226
226
-
 227
227
-
 228
228
-
 229
229
-
 230
230
-
 231
231
-
 232
232
-
 233
233
-
 234
234
-
 235
235
-
 236
236
-
 237
237
-
 238
238
-
 239
239
-
 240
240
-
 241
241
-
 242
242
-
 243
243
-
 244
244
-
 245
245
-
 246
246
-
 247
247
-
 248
248
-
 249
249
-
 250
250
-
 251
251
-
 252
252
-
 253
253
-
 254
254
-
 255
255
-
 256
256
-
 257
257
-
 258
258
-
 259
259
-
 260
260
-
 261
261
-
 262
262
-
 263
263
-
 264
264
-
 265
265
-
 266
266
-
 267
267
-
 268
268
-
 269
269
-
 270
270
-
 271
271
-
 272
272
-
 273
273
-
 274
274
-
 275
275
-
 276
276
-
 277
277
-
 278
278
-
 279
279
-
 280
280
-
 281
281
-
 282
282
-
 283
283
-
 284
284
-
 285
285
-
 286
286
-
 287
287
-
 288
288
-
 289
289
-
 290
290
-
 291
291
-
 292
292
-
 293
293
-
 294
294
-
 295
295
-
 296
296
-
 297
297
-
 298
298
-
 299
299
-
 300
300
-
 301
301
-
 302
302
-
 303
303
-
 304
304
-
 305
305
-
 306
306
-
 307
307
-
 308
308
-
 309
309
-
 310
310
-
 311
311
-
 312
312
-
 313
313
-
 314
314
-
 315
315
-
 316
316
-
 317
317
-
 318
318
-
 319
319
-
 320
320
-
 321
321
-
 322
322
-
 323
323
-
 324
324
-
 325
325
F-SECURE ANTI-VIRUS FOR MICROSOFT EXCHANGE 8.00 - Owner's manual
- Category
- Antivirus security software
- Type
- Owner's manual
- This manual is also suitable for
Ask a question and I''ll find the answer in the document
Finding information in a document is now easier with AI
Related papers
-
F-SECURE CLIENT SECURITY 7.00 Owner's manual
-
F-SECURE ANTI-VIRUS FOR MICROSOFT EXCHANGE 9.00 Administrator's Manual
-
F-SECURE POLICY MANAGER 8.0 Administrator's Manual
-
F-SECURE MOBILE SECURITY 80 Series User manual
-
F-SECURE MOBILE SECURITY 3.0 FOR S60 User manual
-
F-SECURE MOBILE SECURITY FOR UIQ - User manual
-
F-SECURE Policy Manager Quick Installation Manual
-
F-SECURE MOBILE SECURITY FOR UIQ - Quick Manual
-
F-SECURE MOBILE SECURITY 3.1 FOR SYMBIAN Owner's manual
-
F-SECURE Mobile Anti-Virus 60 Series User manual
Other documents
-
 Hauri VRWS351 Datasheet
Hauri VRWS351 Datasheet
-
KAPERSKY ANTI-VIRUS 5.0 - FOR LINUX FREEBSD-OPENBSD FILE SERVER User manual
-
Symantec AntiVirus Corporate Edition Client Manual
-
AVG Internet Security 8.5 - 10 lic. - 1 year User manual
-
AVG Internet Security 2012 User guide
-
TrustPort Total Protection 2013, 1u, 1Y User guide
-
AVG Anti-Virus 2012 User manual
-
Symantec Norton AntiVirus 2005 User manual
-
Symantec 20032623 - Endpoint Protection Small Business Edition Implementation Manual
-
AVG Internet Security 2014 User guide





































































































































































































































































































































