HPE FlexFabric 12900E & 12900 & 7900 Switch Series Security Configuration Guide
- Category
- Software
- Type
- Configuration Guide

HPE FlexFabric
12900E & 12900 & 7900 Switch Series
Security Configuration Guide
HPE FlexFabric 12900E Switch Series
HPE FlexFabric 12900 Switch Series
HPE FlexFabric 7900 Switch
Series
P
art number: 5200-4951f
Software
version: Release 2710 and later
Document version: 6W105-20230612

© Copyright 2022, 2023 Hewlett Packard Enterprise Development LP
The information contained herein is subject to change without notice. The only warranties for Hewlett Packard
Enterprise products and services are set forth in the express warranty statements accompanying such
products and services. Nothing herein should be construed as constituting an additional warranty. Hewlett
Packard Enterprise shall not be liable for technical or editorial errors or omissions contained herein.
Confidential computer software. Valid license from Hewlett Packard Enterprise required for possession, use, or
copying. Consistent with FAR 12.211 and 12.212, Commercial Computer Software, Computer Software
Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under vendor’s
standard commercial license.
Links to third-party websites take you outside the Hewlett Packard Enterprise website. Hewlett Packard
Enterprise has no control over and is not responsible for information outside the Hewlett Packard Enterprise
website.
Acknowledgments
Intel®, Itanium®, Pentium®, Intel Inside®, and the Intel Inside logo are trademarks of Intel Corporation in the
United States and other countries.
Microsoft® and Windows® are either registered trademarks or trademarks of Microsoft Corporation in the
United States and/or other countries.
Adobe® and Acrobat® are trademarks of Adobe Systems Incorporated.
Java and Oracle are registered trademarks of Oracle and/or its affiliates.
UNIX® is a registered trademark of The Open Group.

i
Contents
Configuring AAA ···························································································· 1
About AAA·························································································································································· 1
AAA implementation ··································································································································· 1
AAA network diagram ································································································································ 1
RADIUS ······················································································································································ 2
HWTACACS ··············································································································································· 5
LDAP ·························································································································································· 8
User management based on ISP domains and user access types·························································· 11
Authentication, authorization, and accounting methods··········································································· 11
AAA extended functions ··························································································································· 12
AAA for VPNs ··········································································································································· 13
Protocols and standards ·························································································································· 13
FIPS compliance ·············································································································································· 13
AAA tasks at a glance ······································································································································ 13
Configuring local users····································································································································· 14
About local users ······································································································································ 14
Local user configuration tasks at a glance ······························································································· 15
Configuring attributes for device management users··············································································· 15
Configuring user group attributes ············································································································· 17
Display and maintenance commands for local users and local user groups ··········································· 18
Configuring RADIUS ········································································································································ 18
RADIUS tasks at a glance ························································································································ 18
Configuring a test profile for RADIUS server status detection ································································· 19
Creating a RADIUS scheme ···················································································································· 20
Specifying RADIUS authentication servers ······························································································ 20
Specifying the RADIUS accounting servers ····························································································· 21
Specifying the shared keys for secure RADIUS communication ····························································· 22
Specifying the MPLS L3VPN instance for a RADIUS scheme································································· 22
Setting the status of RADIUS servers ······································································································ 23
Setting RADIUS timers ····························································································································· 24
Specifying the source IP address for outgoing RADIUS packets····························································· 25
Setting the username format and traffic statistics units ············································································ 26
Setting the maximum number of RADIUS request transmission attempts ··············································· 27
Setting the maximum number of real-time accounting attempts ······························································ 27
Setting the DSCP priority for RADIUS packets ························································································ 28
Configuring the Login-Service attribute check method for SSH, FTP, and terminal users ······················ 28
Interpreting the RADIUS class attribute as CAR parameters ··································································· 28
Configuring the MAC address format for RADIUS attribute 31 ································································ 29
Setting the data measurement unit for the Remanent_Volume attribute ················································· 29
Configuring the RADIUS attribute translation feature ·············································································· 30
Configuring RADIUS stop-accounting packet buffering ··········································································· 31
Enabling forcibly sending stop-accounting packets ················································································· 32
Enabling the RADIUS server load sharing feature ··················································································· 32
Configuring the RADIUS accounting-on feature ······················································································ 33
Configuring the RADIUS session-control feature ····················································································· 33
Configuring the RADIUS DAS feature ······································································································ 34
Enabling SNMP notifications for RADIUS ································································································ 34
Display and maintenance commands for RADIUS ·················································································· 35
Configuring HWTACACS ································································································································· 35
HWTACACS tasks at a glance················································································································· 35
Creating an HWTACACS scheme ··········································································································· 36
Specifying the HWTACACS authentication servers ················································································· 36
Specifying the HWTACACS authorization servers ··················································································· 37
Specifying the HWTACACS accounting servers ······················································································ 37
Specifying the shared keys for secure HWTACACS communication ······················································ 38
Specifying an MPLS L3VPN instance for the scheme ············································································· 38
Setting HWTACACS timers ······················································································································ 39

ii
Specifying the source IP address for outgoing HWTACACS packets······················································ 40
Setting the username format and traffic statistics units ············································································ 41
Configuring HWTACACS stop-accounting packet buffering ···································································· 42
Display and maintenance commands for HWTACACS ··········································································· 42
Configuring LDAP ············································································································································ 43
LDAP tasks at a glance ···························································································································· 43
Creating an LDAP server ························································································································· 43
Configuring the IP address of the LDAP server ······················································································· 43
Specifying the LDAP version ···················································································································· 43
Setting the LDAP server timeout period ··································································································· 44
Configuring administrator attributes ········································································································· 44
Configuring LDAP user attributes············································································································· 45
Configuring an LDAP attribute map ········································································································· 46
Creating an LDAP scheme ······················································································································· 46
Specifying the LDAP authentication server ······························································································ 46
Specifying the LDAP authorization server ································································································ 46
Specifying an LDAP attribute map for LDAP authorization ······································································ 47
Display and maintenance commands for LDAP······················································································· 47
Creating an ISP domain ··································································································································· 47
About ISP domains ·································································································································· 47
Restrictions and guidelines for the default ISP domain ············································································ 48
Creating an ISP domain ··························································································································· 48
Specifying the default ISP domain ··········································································································· 48
Specifying an ISP domain for users that are assigned to nonexistent domains ······································ 48
Configuring ISP domain attributes ··················································································································· 49
Setting ISP domain status ························································································································ 49
Configuring authorization attributes for an ISP domain············································································ 49
Including the idle timeout period in the user online duration to be sent to the server ······························ 49
Configuring AAA methods for an ISP domain ·································································································· 50
Configuring authentication methods for an ISP domain ··········································································· 50
Configuring authorization methods for an ISP domain ············································································· 51
Configuring accounting methods for an ISP domain ················································································ 52
Display and maintenance commands for ISP domains············································································ 52
Setting the maximum number of concurrent login users ·················································································· 53
Configuring a NAS-ID······································································································································· 53
Configuring the device ID ································································································································· 53
Configuring the connection recording policy ···································································································· 54
About the connection recording policy ····································································································· 54
Restrictions and guidelines ······················································································································ 54
Procedure ················································································································································· 54
Display and maintenance commands for the connection recording policy ·············································· 54
AAA configuration examples ···························································································································· 55
Example: Configuring AAA for SSH users by an HWTACACS server ····················································· 55
Example: Configuring local authentication, HWTACACS authorization, and RADIUS accounting for SSH
users ························································································································································ 56
Example: Configuring authentication and authorization for SSH users by a RADIUS server ·················· 58
Example: Configuring authentication for SSH users by an LDAP server ················································· 61
Troubleshooting AAA ······································································································································· 66
RADIUS authentication failure ················································································································· 66
RADIUS packet delivery failure ················································································································ 66
RADIUS accounting error ························································································································· 67
Troubleshooting HWTACACS ·················································································································· 67
LDAP authentication failure ······················································································································ 67
Appendixes ······················································································································································ 68
Appendix A Commonly used RADIUS attributes ····················································································· 68
Appendix B Descriptions for commonly used standard RADIUS attributes ············································· 69
Appendix C RADIUS subattributes (vendor ID 25506) ············································································ 71
Configuring password control ······································································ 75
About password control···································································································································· 75
Password setting ······································································································································ 75
Password updating and expiration ··········································································································· 76

iii
User login control ····································································································································· 77
Password not displayed in any form ········································································································ 78
Logging ···················································································································································· 78
FIPS compliance ·············································································································································· 78
Restrictions and guidelines: Password control configuration ··········································································· 78
Password control tasks at a glance·················································································································· 79
Enabling password control ······························································································································· 79
Setting global password control parameters ···································································································· 80
Setting user group password control parameters ···························································································· 82
Setting local user password control parameters ······························································································ 83
Setting super password control parameters····································································································· 84
Display and maintenance commands for password control ············································································· 84
Password control configuration examples ······································································································· 85
Example: Configuring password control ··································································································· 85
Configuring keychains ················································································· 88
About keychains ··············································································································································· 88
Restrictions and guidelines: Keychain configuration ························································································ 88
Configuring a keychain····································································································································· 88
Display and maintenance commands for keychain ·························································································· 89
Keychain configuration example ······················································································································ 89
Example: Configuring keychains ·············································································································· 89
Managing public keys ·················································································· 95
About public key management ························································································································· 95
Asymmetric key algorithm overview ········································································································· 95
Usage of asymmetric key algorithms ······································································································· 95
FIPS compliance ·············································································································································· 95
Public key management tasks at a glance ······································································································· 95
Creating a local key pair··································································································································· 96
Distributing a local host public key ··················································································································· 97
About distribution of local host public keys ······························································································ 97
Exporting a host public key ······················································································································ 97
Displaying a host public key ····················································································································· 98
Configuring a peer host public key ··················································································································· 98
About peer host public key configuration ································································································· 98
Restrictions and guidelines for peer host public key configuration ·························································· 99
Importing a peer host public key from a public key file ············································································ 99
Entering a peer host public key ················································································································ 99
Destroying a local key pair ····························································································································· 100
Display and maintenance commands for public keys ···················································································· 100
Examples of public key management ············································································································ 100
Example: Entering a peer host public key ······························································································ 100
Example: Importing a public key from a public key file ·········································································· 102
Configuring PKI ························································································· 105
About PKI ······················································································································································· 105
PKI terminology ······································································································································ 105
PKI architecture ······································································································································ 106
Retrieval, usage, and maintenance of a digital certificate ······································································ 107
PKI applications ····································································································································· 107
Support for MPLS L3VPN ······················································································································ 107
FIPS compliance ············································································································································ 108
PKI tasks at a glance ····································································································································· 108
Configuring a PKI entity ································································································································· 109
Configuring a PKI domain ······························································································································ 110
About PKI domain ·································································································································· 110
PKI domain tasks at a glance ················································································································· 110
Creating a PKI domain ··························································································································· 110
Specifying the trusted CA ······················································································································· 111
Specifying the PKI entity name ·············································································································· 111
Specifying the certificate request reception authority············································································· 111

iv
Specifying the certificate request URL ··································································································· 111
Setting the SCEP polling interval and maximum polling attempts ························································· 112
Specifying the LDAP server ··················································································································· 112
Specifying the fingerprint for root CA certificate verification··································································· 112
Specifying the key pair for certificate request ························································································ 112
Specifying the intended purpose for the certificate ················································································ 113
Specifying the source IP address for PKI protocol packets ··································································· 113
Specifying the storage path for certificates and CRLs ··················································································· 114
Requesting a certificate·································································································································· 114
About certificate request configuration ··································································································· 114
Restrictions and guidelines for certificate request configuration ···························································· 115
Prerequisites for certificate request configuration ·················································································· 115
Enabling the automatic online certificate request mode········································································· 115
Manually submitting an online certificate request ·················································································· 116
Manually submitting a certificate request in offline mode ······································································· 116
Aborting a certificate request ························································································································· 117
Obtaining certificates······································································································································ 117
Verifying PKI certificates ································································································································ 118
About certification verification ················································································································ 118
Restrictions and guidelines for certificate verification ············································································ 119
Verifying certificates with CRL checking ································································································ 119
Verifying certificates without CRL checking ··························································································· 120
Exporting certificates ······································································································································ 120
Removing a certificate···································································································································· 121
Configuring a certificate-based access control policy ···················································································· 122
About certificate-based access control policies ····················································································· 122
Procedure ··············································································································································· 122
Display and maintenance commands for PKI ································································································ 123
PKI configuration examples ··························································································································· 123
Example: Requesting a certificate from an RSA Keon CA server ·························································· 123
Example: Requesting a certificate from a Windows Server 2003 CA server ········································· 126
Example: Requesting a certificate from an OpenCA server ··································································· 130
Example: Configuring IKE negotiation with RSA digital signature from a Windows Server 2003 CA server
······························································································································································· 133
Example: Configuring a certificate-based access control policy ···························································· 135
Example: Importing and exporting certificates ······················································································· 137
Troubleshooting PKI configuration ················································································································· 142
Failed to obtain the CA certificate ·········································································································· 142
Failed to obtain local certificates ············································································································ 143
Failed to request local certificates ·········································································································· 144
Failed to obtain CRLs ····························································································································· 144
Failed to import the CA certificate ·········································································································· 145
Failed to import the local certificate ········································································································ 145
Failed to export certificates ···················································································································· 146
Failed to set the storage path ················································································································· 146
Configuring IPsec ······················································································ 148
About IPsec ···················································································································································· 148
IPsec framework ···································································································································· 148
IPsec security services ··························································································································· 148
Benefits of IPsec ···································································································································· 148
Security protocols ··································································································································· 148
Encapsulation modes ····························································································································· 149
Security association ······························································································································· 150
Authentication and encryption ················································································································ 150
IPsec-protected traffic ···························································································································· 151
ACL-based IPsec ··································································································································· 151
IPv6 routing protocol-based IPsec ········································································································· 152
IPsec policy and IPsec profile ················································································································ 152
IPsec RRI ··············································································································································· 153
Protocols and standards ························································································································ 154
FIPS compliance ············································································································································ 154

v
Restrictions and guidelines: IPsec configuration···························································································· 154
Implementing ACL-based IPsec····················································································································· 154
ACL-based IPsec tasks at a glance ······································································································· 154
Configuring an ACL ································································································································ 155
Configuring an IPsec transform set ········································································································ 158
Configuring a manual IPsec policy ········································································································· 160
Configuring an IKE-based IPsec policy ·································································································· 162
Applying an IPsec policy to an interface ································································································ 165
Enabling ACL checking for de-encapsulated packets ············································································ 165
Configuring IPsec anti-replay ················································································································· 166
Configuring IPsec anti-replay redundancy ····························································································· 166
Binding a source interface to an IPsec policy ························································································ 167
Enabling QoS pre-classify ······················································································································ 168
Configuring the DF bit of IPsec packets ································································································· 168
Configuring IPsec RRI ···························································································································· 169
Configuring IPsec for IPv6 routing protocols ·································································································· 170
IPsec protection for IPv6 routing protocols tasks at a glance ································································ 170
Configuring a manual IPsec profile ········································································································ 170
Applying the IPsec profile to an IPv6 routing protocol ············································································ 171
Configuring the global IPsec SA lifetime and idle timeout·············································································· 172
Configuring IPsec fragmentation ···················································································································· 172
Setting the maximum number of IPsec tunnels ····························································································· 173
Enabling logging for IPsec packets ················································································································ 173
Configuring SNMP notifications for IPsec ······································································································ 173
Display and maintenance commands for IPsec ····························································································· 174
IPsec configuration examples ························································································································ 175
Example: Configuring a manual mode IPsec tunnel for IPv4 packets ··················································· 175
Example: Configuring an IKE-based IPsec tunnel for IPv4 packets ······················································ 177
Example: Configuring IPsec for RIPng ··································································································· 180
Example: Configuring IPsec RRI ············································································································ 183
Configuring IKE ························································································· 188
About IKE ······················································································································································· 188
Benefits of IKE ······································································································································· 188
Relationship between IPsec and IKE ····································································································· 188
IKE negotiation process ························································································································· 188
IKE security mechanism ························································································································· 190
Protocols and standards ························································································································ 190
FIPS compliance ············································································································································ 191
IKE tasks at a glance ····································································································································· 191
Prerequisites for IKE configuration················································································································· 191
Configuring an IKE profile ······························································································································ 192
Creating an IKE profile ··························································································································· 192
Configuring peer IDs for the IKE profile ································································································· 192
Specifying the IKE keychain or PKI domain ··························································································· 192
Configuring the IKE phase 1 negotiation mode ······················································································ 193
Specifying IKE proposals for the IKE profile ·························································································· 193
Configuring the local ID for the IKE profile ····························································································· 194
Specifying an inside VPN instance for the IKE profile ············································································ 194
Configuring optional features for the IKE profile ···················································································· 194
Configuring an IKE proposal ·························································································································· 195
Configuring an IKE keychain ·························································································································· 197
Configuring the global identity information ····································································································· 198
Configuring the IKE keepalive feature ··········································································································· 198
Configuring the IKE NAT keepalive feature ··································································································· 199
Configuring global IKE DPD ··························································································································· 199
Enabling invalid SPI recovery ························································································································ 200
Setting the maximum number of IKE SAs ······································································································ 200
Configuring an IKE IPv4 address pool ··········································································································· 201
Configuring SNMP notifications for IKE ········································································································· 201
Display and maintenance commands for IKE ································································································ 202
IKE configuration examples ··························································································································· 202

vi
Example: Configuring main-mode IKE with pre-shared key authentication ··········································· 202
Example: Configuring an IKE-based IPsec tunnel for IPv4 packets ······················································ 205
Troubleshooting IKE······································································································································· 207
IKE negotiation failed because no matching IKE proposals were found ················································ 207
IKE negotiation failed because no IKE proposals or IKE keychains are specified correctly ·················· 208
IPsec SA negotiation failed because no matching IPsec transform sets were found ···························· 209
IPsec SA negotiation failed due to invalid identity information ······························································· 209
Configuring IKEv2 ······················································································ 212
About IKEv2 ··················································································································································· 212
IKEv2 negotiation process ····················································································································· 212
New features in IKEv2 ···························································································································· 213
Protocols and standards ························································································································ 213
IKEv2 tasks at a glance·································································································································· 213
Prerequisites for IKEv2 configuration ············································································································· 214
Configuring an IKEv2 profile ·························································································································· 214
Creating an IKEv2 profile ······················································································································· 214
Specifying the local and remote identity authentication methods ·························································· 215
Configuring the IKEv2 keychain or PKI domain ····················································································· 215
Configuring the local ID for the IKEv2 profile ························································································· 215
Configuring peer IDs for the IKEv2 profile······························································································ 216
Specifying a VPN instance for the IKEv2 profile ···················································································· 216
Specifying an inside VPN instance for the IKEv2 profile ········································································ 217
Configuring optional features for the IKEv2 profile ················································································· 217
Configuring an IKEv2 policy ··························································································································· 218
Configuring an IKEv2 proposal ······················································································································ 219
Configuring an IKEv2 keychain ······················································································································ 220
Configure global IKEv2 parameters ··············································································································· 221
Enabling the cookie challenging feature ································································································ 221
Configuring the IKEv2 DPD feature ······································································································· 221
Configuring the IKEv2 NAT keepalive feature ························································································ 222
Configuring IKEv2 address pools ··········································································································· 222
Display and maintenance commands for IKEv2 ···························································································· 223
Troubleshooting IKEv2 ··································································································································· 223
IKEv2 negotiation failed because no matching IKEv2 proposals were found ········································ 223
IPsec SA negotiation failed because no matching IPsec transform sets were found ···························· 224
IPsec tunnel establishment failed ··········································································································· 224
Configuring SSH ························································································ 225
About SSH ····················································································································································· 225
SSH applications ···································································································································· 225
How SSH works ····································································································································· 225
SSH authentication methods ·················································································································· 226
SSH support for Suite B ························································································································· 227
FIPS compliance ············································································································································ 227
Configuring the device as an SSH server ······································································································ 228
SSH server tasks at a glance ················································································································· 228
Generating local key pairs ······················································································································ 228
Specifying the SSH service port ············································································································· 229
Enabling the Stelnet server ···················································································································· 229
Enabling the SFTP server ······················································································································ 230
Enabling the SCP server ························································································································ 230
Enabling NETCONF over SSH ·············································································································· 230
Configuring the user lines for SSH login ································································································ 231
Configuring a client's host public key ····································································································· 231
Configuring an SSH user ······················································································································· 232
Configuring the SSH management parameters ····················································································· 234
Specifying a PKI domain for the SSH server ························································································· 236
Disconnecting SSH sessions ················································································································· 236
Configuring the device as an Stelnet client ···································································································· 236
Stelnet client tasks at a glance··············································································································· 236
Generating local key pairs ······················································································································ 237

vii
Specifying the source IP address for outgoing SSH packets ································································· 237
Establishing a connection to an Stelnet server ······················································································ 238
Deleting server public keys saved in the public key file on the Stelnet client········································· 239
Establishing a connection to an Stelnet server based on Suite B ·························································· 240
Configuring the device as an SFTP client ······································································································ 240
SFTP client tasks at a glance ················································································································· 240
Generating local key pairs ······················································································································ 240
Specifying the source IP address for outgoing SFTP packets ······························································· 241
Establishing a connection to an SFTP server ························································································ 241
Deleting server public keys saved in the public key file on the SFTP client··········································· 243
Establishing a connection to an SFTP server based on Suite B ···························································· 243
Working with SFTP directories ··············································································································· 244
Working with SFTP files ························································································································· 245
Displaying help information ···················································································································· 245
Terminating the connection with the SFTP server ················································································· 246
Configuring the device as an SCP client ········································································································ 246
SCP client tasks at a glance ·················································································································· 246
Generating local key pairs ······················································································································ 246
Specifying the source IP address for outgoing SCP packets ································································· 247
Establishing a connection to an SCP server ·························································································· 247
Deleting server public keys saved in the public key file on the SCP client ············································ 249
Establishing a connection to an SCP server based on Suite B······························································ 249
Specifying algorithms for SSH2 ····················································································································· 250
About algorithms for SSH2 ····················································································································· 250
Specifying key exchange algorithms for SSH2 ······················································································ 250
Specifying public key algorithms for SSH2 ···························································································· 250
Specifying encryption algorithms for SSH2 ···························································································· 251
Specifying MAC algorithms for SSH2 ···································································································· 251
Display and maintenance commands for SSH ······························································································ 251
Stelnet configuration examples ······················································································································ 252
Example: Configuring the device as an Stelnet server (password authentication) ································ 252
Example: Configuring the device as an Stelnet server (publickey authentication) ································· 255
Example: Configuring the device as an Stelnet client (password authentication) ·································· 260
Example: Configuring the device as an Stelnet client (publickey authentication) ·································· 264
Example: Configuring Stelnet based on 128-bit Suite B algorithms······················································· 266
SFTP configuration examples ························································································································ 270
Example: Configuring the device as an SFTP server (password authentication) ·································· 270
Example: Configuring the device as an SFTP client (publickey authentication) ···································· 273
Example: Configuring SFTP based on 192-bit Suite B algorithms························································· 276
SCP configuration examples ·························································································································· 280
Example: Configuring SCP with password authentication ····································································· 280
Example: Configuring SCP file transfer with a Linux SCP client ···························································· 282
Example: Configuring SCP based on Suite B algorithms ······································································ 283
NETCONF over SSH configuration examples ······························································································· 290
Example: Configuring NETCONF over SSH with password authentication ··········································· 290
Configuring SSL ························································································ 293
About SSL ······················································································································································ 293
SSL security services ····························································································································· 293
SSL protocol stack ································································································································· 293
SSL protocol versions ···························································································································· 294
FIPS compliance ············································································································································ 294
Restrictions and guidelines: SSL configuration ······························································································ 294
SSL tasks at a glance ···································································································································· 294
Configuring the SSL server ···················································································································· 294
Configuring the SSL client ······················································································································ 295
Configuring an SSL server policy ··················································································································· 295
Configuring an SSL client policy ···················································································································· 296
Disabling SSL protocol versions for the SSL server ······················································································ 297
Disabling SSL session renegotiation·············································································································· 297
Display and maintenance commands for SSL ······························································································· 298

viii
Configuring object groups ·········································································· 299
About object groups ······································································································································· 299
Restrictions and guidelines: Object group configuration ················································································ 299
Configuring an IPv4 address object group ····································································································· 299
Configuring an IPv6 address object group ····································································································· 299
Configuring a port object group ······················································································································ 300
Display and maintenance commands for object groups ················································································ 300
Configuring attack detection and prevention ·············································· 301
About attack detection and prevention ··········································································································· 301
Attacks that the device can prevent ··············································································································· 301
Single-packet attacks ····························································································································· 301
Scanning attacks ···································································································································· 302
Flood attacks ·········································································································································· 303
TCP fragment attack ······························································································································ 304
Login dictionary attack ··························································································································· 304
Attack detection and prevention tasks at a glance ························································································· 304
Configuring and applying an attack defense policy ························································································ 305
Creating an attack defense policy ·········································································································· 305
Configuring a single-packet attack defense policy ················································································· 305
Configuring a scanning attack defense policy ························································································ 306
Configuring a flood attack defense policy ······························································································ 307
Configuring attack detection exemption ································································································· 312
Applying an attack defense policy to the device ···················································································· 312
Enabling log non-aggregation for single-packet attack events ······································································ 313
Configuring TCP fragment attack prevention ································································································· 313
Enabling the login delay ································································································································· 314
Display and maintenance commands for attack detection and prevention ···················································· 314
Configuring TCP attack prevention ···························································· 318
About TCP attack prevention ························································································································· 318
Configuring Naptha attack prevention ············································································································ 318
Configuring IP source guard ······································································ 319
About IPSG ···················································································································································· 319
IPSG operating mechanism ··················································································································· 319
Static IPSG bindings ······························································································································ 319
Dynamic IPSG bindings ························································································································· 320
Restrictions and guidelines: IPSG configuration ···························································································· 320
IPSG tasks at a glance··································································································································· 321
Configuring the IPv4SG feature ····················································································································· 321
Enabling IPv4SG on an interface ··········································································································· 321
Configuring a static IPv4SG binding ······································································································ 321
Configuring the IPv6SG feature ····················································································································· 322
Enabling IPv6SG on an interface ··········································································································· 322
Configuring a static IPv6SG binding ······································································································ 323
Display and maintenance commands for IPSG ····························································································· 323
IPSG configuration examples ························································································································ 324
Example: Configuring static IPv4SG ······································································································ 324
Example: Configuring DHCP snooping-based dynamic IPv4SG ··························································· 326
Example: Configuring DHCP relay agent-based dynamic IPv4SG ························································ 327
Example: Configuring static IPv6SG ······································································································ 328
Example: Configuring DHCPv6 snooping-based dynamic IPv6SG address bindings ··························· 328
Example: Configuring DHCPv6 snooping-based dynamic IPv6SG prefix bindings ······························· 330
Example: Configuring DHCPv6 relay agent-based dynamic IPv6SG ···················································· 331
Configuring ARP attack protection ····························································· 333
About ARP attack protection ·························································································································· 333
ARP attack protection tasks at a glance ········································································································ 333
Configuring unresolvable IP attack protection ······························································································· 333
About unresolvable IP attack protection································································································· 333

ix
Configuring ARP source suppression ···································································································· 334
Configuring ARP blackhole routing ········································································································ 334
Display and maintenance commands for unresolvable IP attack protection ·········································· 335
Example: Configuring unresolvable IP attack protection········································································ 335
Configuring ARP packet rate limit ·················································································································· 336
Configuring source MAC-based ARP attack detection ·················································································· 337
About source MAC-based ARP attack detection ··················································································· 337
Restrictions and guidelines ···················································································································· 337
Procedure ··············································································································································· 337
Display and maintenance commands for source MAC-based ARP attack detection····························· 338
Example: Configuring source MAC-based ARP attack detection ·························································· 338
Configuring ARP packet source MAC consistency check ·············································································· 339
About ARP packet source MAC consistency check ··············································································· 339
Procedure ··············································································································································· 340
Configuring ARP active acknowledgement ···································································································· 340
Configuring authorized ARP··························································································································· 340
About authorized ARP ···························································································································· 340
Procedure ··············································································································································· 340
Example: Configuring authorized ARP on a DHCP server ···································································· 341
Example: Configuring authorized ARP on a DHCP relay agent ····························································· 342
Configuring ARP attack detection ·················································································································· 343
About ARP attack detection ··················································································································· 343
Configuring user validity check ·············································································································· 344
Configuring ARP packet validity check ·································································································· 345
Configuring ARP restricted forwarding ··································································································· 346
Ignoring ingress ports of ARP packets during user validity check ························································· 346
Enabling ARP attack detection logging ·································································································· 347
Display and maintenance commands for ARP attack detection ···························································· 347
Example: Configuring user validity check and ARP packet validity check ············································· 348
Example: Configuring ARP restricted forwarding ··················································································· 349
Configuring ARP scanning and fixed ARP ····································································································· 351
Configuring ARP gateway protection ············································································································· 352
About ARP gateway protection ·············································································································· 352
Restrictions and guidelines ···················································································································· 352
Procedure ··············································································································································· 352
Example: Configuring ARP gateway protection ····················································································· 353
Configuring ARP filtering ································································································································ 354
ARP filtering ··········································································································································· 354
Restrictions and guidelines ···················································································································· 354
Procedure ··············································································································································· 354
Example: Configuring ARP filtering ········································································································ 354
Configuring ARP sender IP address checking ······························································································· 355
About ARP sender IP address checking ································································································ 355
Restrictions and guidelines ···················································································································· 355
Procedure ··············································································································································· 356
Example: Configuring ARP sender IP address checking ······································································· 356
Configuring ND attack defense ·································································· 358
About ND attack defense ······························································································································· 358
Enabling source MAC consistency check for ND messages ········································································· 358
Configuring uRPF ······················································································ 360
About uRPF···················································································································································· 360
uRPF application scenario ····················································································································· 360
uRPF check modes ································································································································ 360
Network application ································································································································ 361
Feature and hardware compatibility ··············································································································· 361
Enabling uRPF globally ·································································································································· 362
Enabling uRPF on an interface ······················································································································ 362
Display and maintenance commands for uRPF ····························································································· 362

x
Configuring FIPS ······················································································· 363
About FIPS ····················································································································································· 363
FIPS security levels ································································································································ 363
FIPS functionality ··································································································································· 363
FIPS self-tests ········································································································································ 363
Restrictions and guidelines: FIPS ·················································································································· 364
Entering FIPS mode ······································································································································· 366
About entering FIPS mode ····················································································································· 366
Restrictions and guidelines ···················································································································· 366
Using the automatic reboot method to enter FIPS mode ······································································· 366
Using the manual reboot method to enter FIPS mode ··········································································· 367
Manually triggering self-tests ························································································································· 368
Exiting FIPS mode ········································································································································· 368
Display and maintenance commands for FIPS ······························································································ 369
FIPS configuration examples ························································································································· 370
Example: Entering FIPS mode through automatic reboot ······································································ 370
Example: Entering FIPS mode through manual reboot·········································································· 371
Example: Exiting FIPS mode through automatic reboot ········································································ 372
Example: Exiting FIPS mode through manual reboot ············································································ 373
Configuring MACsec ·················································································· 375
About MACsec ··············································································································································· 375
Basic concepts ······································································································································· 375
MACsec services ··································································································································· 375
MACsec application mode ····················································································································· 376
MACsec operating mechanism ·············································································································· 376
Protocols and standards ························································································································ 377
Restrictions: Hardware compatibility with MACsec ························································································ 377
Restrictions and guidelines: MACsec configuration ······················································································· 377
MACsec tasks at a glance······························································································································ 377
Enabling MKA ················································································································································ 377
Enabling MACsec desire ································································································································ 378
Configuring a preshared key ·························································································································· 378
Specifying a cipher suite for MACsec encryption ··························································································· 379
Configuring the MKA key server priority ········································································································ 379
Configuring MACsec protection parameters ·································································································· 380
About MACsec protection parameters ··································································································· 380
Restrictions and guidelines for MACsec protection parameter configuration········································· 380
Configuring MACsec protection parameters in interface view ······························································· 380
Configuring MACsec protection parameters by MKA policy ·································································· 381
Enabling MKA session logging······················································································································· 382
Display and maintenance commands for MACsec ························································································ 382
MACsec configuration examples···················································································································· 383
Example: Configuring device-oriented MACsec····················································································· 383
Troubleshooting MACsec ······························································································································· 386
Cannot establish MKA sessions between MACsec devices ·································································· 386
Configuring crypto engines ········································································ 388
About crypto engines ····································································································································· 388
Restrictions: Software compatibility with crypto engine ················································································· 388
Display and maintenance commands for crypto engines ·············································································· 388
Document conventions and icons ······························································ 389
Conventions ··················································································································································· 389
Network topology icons ·································································································································· 390
Support and other resources ····································································· 391
Accessing Hewlett Packard Enterprise Support····························································································· 391
Accessing updates ········································································································································· 391
Websites ················································································································································ 392
Customer self repair ······························································································································· 392

xi
Remote support ······································································································································ 392
Documentation feedback ······················································································································· 392
Index ·········································································································· 394

1
Configuring AAA
About AAA
AAA implementation
Authentication, Authorization, and Accounting (AAA) provides a uniform framework for implementing
network access management. This feature specifies the following security functions:
•
Authentication—Identifies users and verifies their validity.
•
Authorization—Grants different users different rights, and controls the users' access to
resources and services. For example, you can permit office users to read and print files and
prevent guests from accessing files on the device.
•
Accounting—Records network usage details of users, including the service type, start time,
and traffic. This function enables time-based and traffic-based charging and user behavior
auditing.
AAA network diagram
AAA uses a client/server model. The client runs on the access device, or the network access server
(NAS), which authenticates user identities and controls user access. The server maintains user
information centrally. See Figure 1.
Figure 1 AAA network diagram
To access networks or resources beyond the NAS, a user sends its identity information to the NAS.
The NAS transparently passes the user information to AAA servers and waits for the authentication,
authorization, and accounting result. Based on the result, the NAS determines whether to permit or
deny the access request.
AAA has various implementations, including HWTACACS, LDAP, and RADIUS. RADIUS is most
often used.
You can use different servers to implement different security functions. For example, you can use an
HWTACACS server for authentication and authorization, and use a RADIUS server for accounting.
You can choose the security functions provided by AAA as needed. For example, if your company
wants employees to be authenticated before they access specific resources, you would deploy an
authentication server. If network usage information is needed, you would also configure an
accounting server.
Remote user NAS RADIUS server
HWTACACS server
Internet
Network

2
The device performs dynamic password authentication.
RADIUS
Remote Authentication Dial-In User Service (RADIUS) is a distributed information interaction
protocol that uses a client/server model. The protocol can protect networks against unauthorized
access and is often used in network environments that require both high security and remote user
access.
The RADIUS authorization process is combined with the RADIUS authentication process, and user
authorization information is piggybacked in authentication responses. RADIUS uses UDP port 1812
for authentication and UDP port 1813 for accounting.
RADIUS was originally designed for dial-in user access, and has been extended to support
additional access methods, such as Ethernet and ADSL.
Client/server model
The RADIUS client runs on the NASs located throughout the network. It passes user information to
RADIUS servers and acts on the responses to, for example, reject or accept user access requests.
The RADIUS server runs on the computer or workstation at the network center and maintains
information related to user authentication and network service access.
The RADIUS server operates using the following process:
1. Receives authentication, authorization, and accounting requests from RADIUS clients.
2. Performs user authentication, authorization, or accounting.
3. Returns user access control information (for example, rejecting or accepting the user access
request) to the clients.
The RADIUS server can also act as the client of another RADIUS server to provide authentication
proxy services.
The RADIUS server maintains the following databases:
•
Users—Stores user information, such as the usernames, passwords, applied protocols, and IP
addresses.
•
Clients—Stores information about RADIUS clients, such as shared keys and IP addresses.
•
Dictionary—Stores RADIUS protocol attributes and their values.
Figure 2 RADIUS server databases
Information exchange security mechanism
The RADIUS client and server exchange information between them with the help of shared keys,
which are preconfigured on the client and server. A RADIUS packet has a 16-byte field called
Authenticator. This field includes a signature generated by using the MD5 algorithm, the shared key,
and some other information. The receiver of the packet verifies the signature and accepts the packet
only when the signature is correct. This mechanism ensures the security of information exchanged
between the RADIUS client and server.
The shared keys are also used to encrypt user passwords that are included in RADIUS packets.
RADIUS servers
Users Clients Dictionary

3
User authentication methods
The RADIUS server supports multiple user authentication methods, such as PAP, CHAP, and EAP.
Basic RADIUS packet exchange process
Figure 3 illustrates the interactions between a user host, the RADIUS client, and the RADIUS server.
Figure 3 Basic RADIUS packet exchange process
RADIUS uses in the following workflow:
1. The host sends a connection request that includes the user's username and password to the
RADIUS client.
2. The RADIUS client sends an authentication request (Access-Request) to the RADIUS server.
The request includes the user's password, which has been processed by the MD5 algorithm
and shared key.
3. The RADIUS server authenticates the username and password. If the authentication succeeds,
the server sends back an Access-Accept packet that contains the user's authorization
information. If the authentication fails, the server returns an Access-Reject packet.
4. The RADIUS client permits or denies the user according to the authentication result. If the result
permits the user, the RADIUS client sends a start-accounting request (Accounting-Request)
packet to the RADIUS server.
5. The RADIUS server returns an acknowledgment (Accounting-Response) packet and starts
accounting.
6. The user accesses the network resources.
7. The host requests the RADIUS client to tear down the connection.
8. The RADIUS client sends a stop-accounting request (Accounting-Request) packet to the
RADIUS server.
9. The RADIUS server returns an acknowledgment (Accounting-Response) and stops accounting
for the user.
10. The RADIUS client notifies the user of the termination.
RADIUS client RADIUS server
1) Username and password
3) Access-Accept/Reject
2) Access-Request
4) Accounting-Request (start)
5) Accounting-Response
8) Accounting-Request (stop)
9) Accounting-Response
10) Notification of termination
Host
6) The host access the resources
7) Teardown request

4
RADIUS packet format
RADIUS uses UDP to transmit packets. The protocol also uses a series of mechanisms to ensure
smooth packet exchange between the RADIUS server and the client. These mechanisms include the
timer mechanism, the retransmission mechanism, and the backup server mechanism.
Figure 4 RADIUS packet format
Descriptions of the fields are as follows:
•
The Code field (1 byte long) indicates the type of the RADIUS packet. Table 1 gives the main
values and their meanings.
Table 1 Main values of the Code field
Code
Packet type
Description
1 Access-Request
From the client to the server. A packet of this type includes user
information for the server to authenticate the user. It must contain the
User-Name attribute and can optionally contain the attributes of
NAS-IP-Address, User-Password, and NAS-Port.
2 Access-Accept From the server to the client. If all attribute values included in the
Access-Request are acceptable, the authentication succeeds, and
the server sends an Access-Accept response.
3 Access-Reject From the server to the client. If any attribute value included in the
Access-Request is unacceptable, the authentication fails, and the
server sends an Access-Reject response.
4 Accounting-Reques
t
From the client to the server. A packet of this type includes user
information for the server to start or stop accounting for the user. The
Acct-Status-Type attribute in the packet indicates whether to start or
stop accounting.
5 Accounting-Respon
se
From the server to the client. The server sends a packet of this type to
notify the client that it has received the Accounting-Request and has
successfully recorded the accounting information.
•
The Identifier field (1 byte long) is used to match response packets with request packets and to
detect duplicate request packets. The request and response packets of the same exchange
process for the same purpose (such as authentication or accounting) have the same identifier.
•
The Length field (2 bytes long) indicates the length of the entire packet (in bytes), including the
Code, Identifier, Length, Authenticator, and Attributes fields. Bytes beyond this length are
considered padding and are ignored by the receiver. If the length of a received packet is less
than this length, the packet is dropped.
•
The Authenticator field (16 bytes long) is used to authenticate responses from the RADIUS
server and to encrypt user passwords. There are two types of authenticators: request
authenticator and response authenticator.
Code
Attributes
Identifier
0
7
Length
Authenticator (16bytes)
7 15 31

5
•
The Attributes field (variable in length) includes authentication, authorization, and accounting
information. This field can contain multiple attributes, each with the following subfields:
Type—Type of the attribute.
Length—Length of the attribute in bytes, including the Type, Length, and Value subfields.
Value—Value of the attribute. Its format and content depend on the Type subfield.
Extended RADIUS attributes
The RADIUS protocol features excellent extensibility. The Vendor-Specific attribute (attribute 26)
allows a vendor to define extended attributes. The extended attributes can implement functions that
the standard RADIUS protocol does not provide.
A vendor can encapsulate multiple subattributes in the TLV format in attribute 26 to provide extended
functions. As shown in Figure 5, a subattribute encapsulated in attribute 26 consists of the following
parts:
•
Vendor-ID—ID of the vendor. The most significant byte is 0. The other three bytes contains a
code compliant to RFC 1700.
•
Vendor-Type—Type of the subattribute.
•
Vendor-Length—Length of the subattribute.
•
Vendor-Data—Contents of the subattribute.
The device supports private RADIUS subattributes with a vendor ID of 25506. For more information,
see "Appendix C RADIUS subattributes (vendor ID 25506)."
Figure 5 Format of attribute 26
HWTACACS
HW Terminal Access Controller Access Control System (HWTACACS) is an enhanced security
protocol based on TACACS (RFC 1492). HWTACACS is similar to RADIUS, and uses a client/server
model for information exchange between the NAS and the HWTACACS server.
HWTACACS typically provides AAA services for PPP, VPDN, and terminal users. In a typical
HWTACACS scenario, terminal users need to log in to the NAS. Working as the HWTACACS client,
the NAS sends users' usernames and passwords to the HWTACACS server for authentication. After
passing authentication and obtaining authorized rights, a user logs in to the device and performs
operations. The HWTACACS server records the operations that each user performs.
Differences between HWTACACS and RADIUS
HWTACACS and RADIUS have many features in common, such as using a client/server model,
using shared keys for data encryption, and providing flexibility and scalability. Table 2 lists the
primary differences between HWTACACS and RADIUS.
Table 2 Primary differences between HWTACACS and RADIUS
HWTACACS
RADIUS
Uses TCP, which provides reliable network
transmission. Uses UDP, which provides high transport efficiency.
Type Length
0
Vendor-ID
7 15 31
Vendor-ID (continued) Vendor-Type Vendor-Length
Vendor-Data
(Specified attribute value……)
23
……

6
HWTACACS
RADIUS
Encrypts the entire packet except for the
HWTACACS header. Encrypts only the user password field in an
authentication packet.
Protocol packets are complicated and authorization
is independent of authentication. Authentication and
authorization can be deployed on different
HWTACACS servers.
Protocol packets are simple and the authorization
process is combined with the authentication
process.
Supports authorization of configuration commands.
Access to commands depends on both the user's
roles and authorization. A user can use only
commands that are permitted by the user roles and
authorized by the HWTACACS server.
Does not support authorization of configuration
commands. Access to commands solely depends on
the user's roles. For more information about user
roles, see Fundamentals Configuration Guide.
Basic HWTACACS packet exchange process
Figure 6 describes how HWTACACS performs user authentication, authorization, and accounting for
a Telnet user.

7
Figure 6 Basic HWTACACS packet exchange process for a Telnet user
HWTACACS operates using in the following workflow:
1. A Telnet user sends an access request to the HWTACACS client.
2. The HWTACACS client sends a start-authentication packet to the HWTACACS server when it
receives the request.
3. The HWTACACS server sends back an authentication response to request the username.
4. Upon receiving the response, the HWTACACS client asks the user for the username.
5. The user enters the username.
6. After receiving the username from the user, the HWTACACS client sends the server a
continue-authentication packet that includes the username.
7. The HWTACACS server sends back an authentication response to request the login password.
8. Upon receipt of the response, the HWTACACS client prompts the user for the login password.
9. The user enters the password.
Host HWTACACS client HWTACACS server
1) The user tries to log in
2) Start-authentication packet
3) Authentication response requesting the username
4) Request for username
5) The user enters the username
6) Continue-authentication packet with the username
7) Authentication response requesting the password
8) Request for password
9) The user enters the password
11) Response indicating successful authentication
12) User authorization request packet
13) Response indicating successful authorization
14) The user logs in successfully
15) Start-accounting request
16) Response indicating the start of accounting
17) The user logs off
18) Stop-accounting request
19) Stop-accounting response
10) Continue-a u th e n tic a tio n packet with the password
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
-
 1
1
-
 2
2
-
 3
3
-
 4
4
-
 5
5
-
 6
6
-
 7
7
-
 8
8
-
 9
9
-
 10
10
-
 11
11
-
 12
12
-
 13
13
-
 14
14
-
 15
15
-
 16
16
-
 17
17
-
 18
18
-
 19
19
-
 20
20
-
 21
21
-
 22
22
-
 23
23
-
 24
24
-
 25
25
-
 26
26
-
 27
27
-
 28
28
-
 29
29
-
 30
30
-
 31
31
-
 32
32
-
 33
33
-
 34
34
-
 35
35
-
 36
36
-
 37
37
-
 38
38
-
 39
39
-
 40
40
-
 41
41
-
 42
42
-
 43
43
-
 44
44
-
 45
45
-
 46
46
-
 47
47
-
 48
48
-
 49
49
-
 50
50
-
 51
51
-
 52
52
-
 53
53
-
 54
54
-
 55
55
-
 56
56
-
 57
57
-
 58
58
-
 59
59
-
 60
60
-
 61
61
-
 62
62
-
 63
63
-
 64
64
-
 65
65
-
 66
66
-
 67
67
-
 68
68
-
 69
69
-
 70
70
-
 71
71
-
 72
72
-
 73
73
-
 74
74
-
 75
75
-
 76
76
-
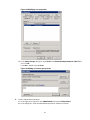 77
77
-
 78
78
-
 79
79
-
 80
80
-
 81
81
-
 82
82
-
 83
83
-
 84
84
-
 85
85
-
 86
86
-
 87
87
-
 88
88
-
 89
89
-
 90
90
-
 91
91
-
 92
92
-
 93
93
-
 94
94
-
 95
95
-
 96
96
-
 97
97
-
 98
98
-
 99
99
-
 100
100
-
 101
101
-
 102
102
-
 103
103
-
 104
104
-
 105
105
-
 106
106
-
 107
107
-
 108
108
-
 109
109
-
 110
110
-
 111
111
-
 112
112
-
 113
113
-
 114
114
-
 115
115
-
 116
116
-
 117
117
-
 118
118
-
 119
119
-
 120
120
-
 121
121
-
 122
122
-
 123
123
-
 124
124
-
 125
125
-
 126
126
-
 127
127
-
 128
128
-
 129
129
-
 130
130
-
 131
131
-
 132
132
-
 133
133
-
 134
134
-
 135
135
-
 136
136
-
 137
137
-
 138
138
-
 139
139
-
 140
140
-
 141
141
-
 142
142
-
 143
143
-
 144
144
-
 145
145
-
 146
146
-
 147
147
-
 148
148
-
 149
149
-
 150
150
-
 151
151
-
 152
152
-
 153
153
-
 154
154
-
 155
155
-
 156
156
-
 157
157
-
 158
158
-
 159
159
-
 160
160
-
 161
161
-
 162
162
-
 163
163
-
 164
164
-
 165
165
-
 166
166
-
 167
167
-
 168
168
-
 169
169
-
 170
170
-
 171
171
-
 172
172
-
 173
173
-
 174
174
-
 175
175
-
 176
176
-
 177
177
-
 178
178
-
 179
179
-
 180
180
-
 181
181
-
 182
182
-
 183
183
-
 184
184
-
 185
185
-
 186
186
-
 187
187
-
 188
188
-
 189
189
-
 190
190
-
 191
191
-
 192
192
-
 193
193
-
 194
194
-
 195
195
-
 196
196
-
 197
197
-
 198
198
-
 199
199
-
 200
200
-
 201
201
-
 202
202
-
 203
203
-
 204
204
-
 205
205
-
 206
206
-
 207
207
-
 208
208
-
 209
209
-
 210
210
-
 211
211
-
 212
212
-
 213
213
-
 214
214
-
 215
215
-
 216
216
-
 217
217
-
 218
218
-
 219
219
-
 220
220
-
 221
221
-
 222
222
-
 223
223
-
 224
224
-
 225
225
-
 226
226
-
 227
227
-
 228
228
-
 229
229
-
 230
230
-
 231
231
-
 232
232
-
 233
233
-
 234
234
-
 235
235
-
 236
236
-
 237
237
-
 238
238
-
 239
239
-
 240
240
-
 241
241
-
 242
242
-
 243
243
-
 244
244
-
 245
245
-
 246
246
-
 247
247
-
 248
248
-
 249
249
-
 250
250
-
 251
251
-
 252
252
-
 253
253
-
 254
254
-
 255
255
-
 256
256
-
 257
257
-
 258
258
-
 259
259
-
 260
260
-
 261
261
-
 262
262
-
 263
263
-
 264
264
-
 265
265
-
 266
266
-
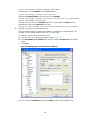 267
267
-
 268
268
-
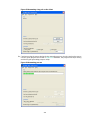 269
269
-
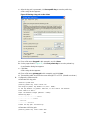 270
270
-
 271
271
-
 272
272
-
 273
273
-
 274
274
-
 275
275
-
 276
276
-
 277
277
-
 278
278
-
 279
279
-
 280
280
-
 281
281
-
 282
282
-
 283
283
-
 284
284
-
 285
285
-
 286
286
-
 287
287
-
 288
288
-
 289
289
-
 290
290
-
 291
291
-
 292
292
-
 293
293
-
 294
294
-
 295
295
-
 296
296
-
 297
297
-
 298
298
-
 299
299
-
 300
300
-
 301
301
-
 302
302
-
 303
303
-
 304
304
-
 305
305
-
 306
306
-
 307
307
-
 308
308
-
 309
309
-
 310
310
-
 311
311
-
 312
312
-
 313
313
-
 314
314
-
 315
315
-
 316
316
-
 317
317
-
 318
318
-
 319
319
-
 320
320
-
 321
321
-
 322
322
-
 323
323
-
 324
324
-
 325
325
-
 326
326
-
 327
327
-
 328
328
-
 329
329
-
 330
330
-
 331
331
-
 332
332
-
 333
333
-
 334
334
-
 335
335
-
 336
336
-
 337
337
-
 338
338
-
 339
339
-
 340
340
-
 341
341
-
 342
342
-
 343
343
-
 344
344
-
 345
345
-
 346
346
-
 347
347
-
 348
348
-
 349
349
-
 350
350
-
 351
351
-
 352
352
-
 353
353
-
 354
354
-
 355
355
-
 356
356
-
 357
357
-
 358
358
-
 359
359
-
 360
360
-
 361
361
-
 362
362
-
 363
363
-
 364
364
-
 365
365
-
 366
366
-
 367
367
-
 368
368
-
 369
369
-
 370
370
-
 371
371
-
 372
372
-
 373
373
-
 374
374
-
 375
375
-
 376
376
-
 377
377
-
 378
378
-
 379
379
-
 380
380
-
 381
381
-
 382
382
-
 383
383
-
 384
384
-
 385
385
-
 386
386
-
 387
387
-
 388
388
-
 389
389
-
 390
390
-
 391
391
-
 392
392
-
 393
393
-
 394
394
-
 395
395
-
 396
396
-
 397
397
-
 398
398
-
 399
399
-
 400
400
-
 401
401
-
 402
402
-
 403
403
-
 404
404
-
 405
405
-
 406
406
-
 407
407
-
 408
408
-
 409
409
-
 410
410
-
 411
411
-
 412
412
-
 413
413
-
 414
414
-
 415
415
-
 416
416
-
 417
417
-
 418
418
-
 419
419
-
 420
420
-
 421
421
-
 422
422
-
 423
423
-
 424
424
-
 425
425
-
 426
426
-
 427
427
-
 428
428
-
 429
429
-
 430
430
-
 431
431
-
 432
432
-
 433
433
-
 434
434
-
 435
435
-
 436
436
-
 437
437
-
 438
438
-
 439
439
-
 440
440
-
 441
441
-
 442
442
-
 443
443
-
 444
444
-
 445
445
-
 446
446
-
 447
447
-
 448
448
-
 449
449
HPE FlexFabric 12900E & 12900 & 7900 Switch Series Security Configuration Guide
- Category
- Software
- Type
- Configuration Guide
Ask a question and I''ll find the answer in the document
Finding information in a document is now easier with AI
Related papers
-
Aruba R9F19A Reference guide
-
Aruba JG091B Configuration Guide
-
Aruba R9F19A Configuration Guide
-
HPE FlexNetwork 7500 Series Security Configuration Manual
-
HPE Networking Comware 5120v3 Switch Series User guide
-
Aruba JL588A Reference guide
-
Aruba JL588A Reference guide
-
HPE About theNetworking Comware 5120v3 Switch Series User guide
-
Aruba JH103A Configuration Guide
-
Aruba JH691A Reference guide
Other documents
-
Aruba R9Y19A Configuration Guide
-
Aruba R9F19A Configuration Guide
-
Aruba R9Y19A Reference guide
-
Aruba Security User guide
-
H3C S5820V2 series Security Configuration Manual
-
H3C MSR Series Command Reference Manual
-
HP 6125XLG Configuration manual
-
HP FlexFabric 5930 Series Security Configuration Manual
-
Aruba 16.05 WC User guide
-
HP 6125G Configuration manual
































































































































































































































































































































































































































































