Aruba FlexFabric 5940 Switch Series EVPN Configuration Guide
- Category
- Networking
- Type
- Configuration Guide

HPE FlexFabric 5940 Switch Series
EVPN Configuration Guide
Software version: Release 671x and later
Document version: 6W100-20230822

© Copyright 2023 Hewlett Packard Enterprise Development LP
The information contained herein is subject to change without notice. The only warranties for Hewlett Packard
Enterprise products and services are set forth in the express warranty statements accompanying such
products and services. Nothing herein should be construed as constituting an additional warranty. Hewlett
Packard Enterprise shall not be liable for technical or editorial errors or omissions contained herein.
Confidential computer software. Valid license from Hewlett Packard Enterprise required for possession, use, or
copying. Consistent with FAR 12.211 and 12.212, Commercial Computer Software, Computer Software
Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under vendor’s
standard commercial license.
Links to third-party websites take you outside the Hewlett Packard Enterprise website. Hewlett Packard
Enterprise has no control over and is not responsible for information outside the Hewlett Packard Enterprise
website.
Acknowledgments
Intel®, Itanium®, Pentium®, Intel Inside®, and the Intel Inside logo are trademarks of Intel Corporation in the
United States and other countries.
Microsoft® and Windows® are either registered trademarks or trademarks of Microsoft Corporation in the
United States and/or other countries.
Adobe® and Acrobat® are trademarks of Adobe Systems Incorporated.
Java and Oracle are registered trademarks of Oracle and/or its affiliates.
UNIX® is a registered trademark of The Open Group.

i
Contents
EVPN overview ······························································································ 1
EVPN solutions ·················································································································································· 1
EVPN VXLAN ············································································································································· 1
EVPN benefits ···················································································································································· 1
Layered transport network ································································································································· 2
MP-BGP extension for EVPN····························································································································· 2
RD and route target selection of BGP EVPN routes ·························································································· 3
EVPN VXLAN overview ················································································· 5
Network model ··················································································································································· 5
Configuration automation ··································································································································· 6
Assignment of traffic to VXLANs ························································································································ 6
Traffic from the local site to a remote site ·································································································· 6
Traffic from a remote site to the local site ·································································································· 7
Layer 2 forwarding ············································································································································· 7
MAC learning ············································································································································· 7
Unicast ······················································································································································· 7
Flood ·························································································································································· 8
Centralized EVPN gateway deployment ············································································································ 9
Distributed EVPN gateway deployment ··········································································································· 10
About distributed EVPN gateway deployment ························································································· 10
Symmetric IRB ········································································································································· 11
Asymmetric IRB ······································································································································· 14
EVPN VXLAN multihoming ······························································································································ 15
About EVPN multihoming ························································································································· 15
DF election ··············································································································································· 16
Split horizon ············································································································································· 17
Redundancy mode ··································································································································· 18
IP aliasing ················································································································································· 18
EVPN VXLAN multicast ··································································································································· 18
Multicast in single-homed sites ················································································································ 19
Multicast in multihomed sites ··················································································································· 19
ARP and ND flood suppression ······················································································································· 20
MAC mobility ···················································································································································· 21
EVPN DRNI······················································································································································ 21
About EVPN DRNI ··································································································································· 22
VM reachability information synchronization ···························································································· 22
Virtual VTEP address ······························································································································· 22
Independent BGP neighbor relationship establishment ··········································································· 22
Site-facing link redundancy ······················································································································ 23
Configuring EVPN VXLAN ··········································································· 24
EVPN VXLAN tasks at a glance ······················································································································ 24
Restrictions and guidelines: EVPN VXLAN configuration ················································································ 25
Setting the VXLAN hardware resource mode ·································································································· 27
Configuring a VXLAN on a VSI ························································································································ 27
Restrictions and guidelines for VXLAN configuration on a VSI ································································ 27
Creating a VXLAN on a VSI ····················································································································· 27
Configuring VSI parameters ····················································································································· 28
Configuring an EVPN instance ························································································································ 28
About EVPN instance configuration ········································································································· 28
Restrictions and guidelines for EVPN instance configuration ·································································· 28
Configuring an EVPN instance created in system view ··········································································· 28
Configuring an EVPN instance created in VSI view ················································································· 29
Configuring EVPN multihoming························································································································ 30
Restrictions and guidelines for EVPN multihoming ·················································································· 30
Assigning an ESI to an interface ·············································································································· 30

ii
Setting the DF election delay ··················································································································· 30
Configuring FRR for EVPN VXLAN ·········································································································· 31
Disabling advertisement of EVPN multihoming routes············································································· 31
Configuring BGP to advertise BGP EVPN routes ···························································································· 31
Restrictions and guidelines for BGP EVPN route advertisement ····························································· 31
Enabling BGP to advertise BGP EVPN routes ························································································· 31
Configuring BGP EVPN route settings ····································································································· 32
Enabling the device to ignore default routes in route recursion ······························································· 35
Maintaining BGP sessions ······················································································································· 36
Mapping ACs to a VSI ······································································································································ 36
Mapping a static Ethernet service instance to a VSI ················································································ 36
Mapping dynamic Ethernet service instances to VSIs ············································································· 37
Configuring a centralized EVPN gateway ········································································································ 39
Restrictions and guidelines for centralized EVPN gateway configuration ················································ 39
Prerequisites for centralized EVPN gateway configuration ······································································ 39
Configuring a centralized gateway interface ···························································································· 39
Setting the static flag for the MAC addresses of centralized gateway interfaces ····································· 39
Configuring a distributed EVPN gateway ········································································································· 40
Restrictions and guidelines for distributed EVPN gateway configuration ················································· 40
Prerequisites for distributed EVPN gateway configuration······································································· 40
Configuring the traffic forwarding mode for EVPN VXLAN ······································································ 41
Configuring a VSI interface ······················································································································ 41
Configuring an L3 VXLAN ID for a VSI interface······················································································ 42
Configuring IP prefix route advertisement ································································································ 45
Configuring BGP route exchange between the public instance and VPN instances ······························· 46
Configuring the EVPN global MAC address····························································································· 48
Disabling generation of IP prefix advertisement routes for the subnets of a VSI interface ······················ 48
Enabling a distributed EVPN gateway to send RA messages over VXLAN tunnels ································ 49
Enabling traffic statistics for the VSIs automatically created for L3 VXLAN IDs ······································ 50
Enabling the device to advertise ARP information for the distributed EVPN gateway interfaces through
MAC/IP advertisement routes ·················································································································· 50
Managing remote MAC address entries and remote ARP or ND learning ······················································· 51
Disabling remote MAC address learning and remote ARP or ND learning ·············································· 51
Disabling MAC address advertisement ···································································································· 51
Enabling MAC mobility event suppression ······························································································· 52
Disabling learning of MAC addresses from ARP or ND information ························································ 52
Disabling ARP information advertisement ································································································ 53
Enabling ND information advertisement··································································································· 54
Disabling the VSI interface on a centralized EVPN gateway from learning ARP or ND information across
subnets ····················································································································································· 54
Enabling ARP mobility event suppression ······························································································· 55
Enabling ND mobility event suppression ·································································································· 56
Enabling ARP request proxy ···················································································································· 56
Enabling ND request proxy ······················································································································ 57
Enabling conversational learning for forwarding entries ·················································································· 58
About conversational learning for forwarding entries ··············································································· 58
Restrictions and guidelines for enabling conversational learning for forwarding entries·························· 58
Enabling conversational learning for remote MAC address entries ························································· 59
Enabling conversational learning for host route FIB entries····································································· 59
Configuring BGP EVPN route redistribution and advertisement ······································································ 60
Redistributing MAC/IP advertisement routes into BGP unicast routing tables ········································· 60
Setting the metric of BGP EVPN routes added to a VPN instance's routing table ··································· 61
Enabling BGP EVPN route advertisement to the local site ······································································ 61
Disabling flooding for a VSI ······························································································································ 62
Enabling ARP or ND flood suppression ··········································································································· 63
Enabling packet statistics for VXLAN tunnels ·································································································· 63
Testing the connectivity of a VXLAN tunnel ····································································································· 64
Enabling overlay OAM ····························································································································· 64
Pinging a VXLAN tunnel destination ········································································································ 64
Tracing the path to a VXLAN tunnel destination ······················································································ 65
Enabling SNMP notifications for EVPN ············································································································ 66
Configuring EVPN DRNI ·································································································································· 66

iii
About this task ·········································································································································· 66
Restrictions and guidelines ······················································································································ 67
Prerequisites ············································································································································ 68
Procedure (IPv4) ······································································································································ 69
Procedure (IPv6) ······································································································································ 70
Display and maintenance commands for EVPN ······························································································ 70
EVPN VXLAN configuration examples ············································································································ 73
Example: Configuring a centralized EVPN gateway ················································································ 73
Example: Configuring distributed EVPN gateways in symmetric IRB mode (IPv4 underlay network) ····· 81
Example: Configuring distributed EVPN gateways in symmetric IRB mode (IPv6 underlay network) ····· 90
Example: Configuring distributed IPv4 EVPN gateways in asymmetric IRB mode ·································· 99
Example: Configuring communication between EVPN networks and the public network ······················ 109
Example: Configuring IPv4 EVPN DRNI with a direct IPL ····································································· 117
Example: Configuring IPv4 EVPN DRNI with a tunnel IPL ···································································· 130
Example: Configuring IPv4 EVPN multihoming ····················································································· 142
Example: Configuring EVPN multicast ··································································································· 150
Configuring EVPN-DCI ·············································································· 158
About EVPN-DCI············································································································································ 158
EVPN-DCI network model ······················································································································ 158
Working mechanisms ····························································································································· 158
EVPN-DCI dual-homing ························································································································· 158
EVPN-DCI DRNI ···································································································································· 159
Restrictions and guidelines: EVPN-DCI configuration ··················································································· 160
EVPN-DCI tasks at a glance ·························································································································· 160
Prerequisites for EVPN-DCI ··························································································································· 161
Enabling DCI ·················································································································································· 161
Configuring an ED to modify BGP EVPN routes ···························································································· 162
Enabling route nexthop replacement and route router MAC replacement ············································· 162
Enabling an ED to replace the L3 VXLAN ID, RD, and route targets of BGP EVPN routes ·················· 163
Suppressing BGP EVPN route advertisement ······························································································· 164
Configuring VXLAN mapping ························································································································· 164
Configuring the BGP EVPN address family and the BGP VPNv4 or VPNv6 address family to exchange routes
······································································································································································· 166
About route exchange ···························································································································· 166
Enabling BGP VPNv4 or VPNv6 route advertisement for the BGP EVPN address family ···················· 166
Enabling BGP EVPN route advertisement for the BGP VPNv4 or VPNv6 address family ···················· 167
Configuring EVPN-DCI dual-homing ·············································································································· 167
Configuring EVPN-DCI DRNI ························································································································· 168
Enabling EVPN-DCI support for cross-VXLAN Layer 2 multicast ·································································· 168
EVPN-DCI configuration examples ················································································································ 169
Example: Configuring a basic EVPN-DCI network ················································································· 169
Example: Configuring EVPN-DCI Layer 3 communication (IPv4 underlay network) ····························· 175
Example: Configuring EVPN-DCI dual-homing ······················································································ 182
Example: Configuring EVPN-DCI DRNI ································································································· 191
MVXLAN overview ····················································································· 202
Restrictions and guidelines: MVXLAN configuration ······················································································ 202
MVXLAN modes············································································································································· 202
Ingress replication MVXLAN ·························································································································· 202
Network model ······································································································································· 202
Working mechanism ······························································································································· 203
MDT MVXLAN················································································································································ 204
Benefits ·················································································································································· 204
Network model ······································································································································· 204
Basic concepts ······································································································································· 204
MP-BGP extension for MVXLAN ············································································································ 205
Automatic MVXLAN tunnel establishment and assignment ··································································· 205
Default MDT establishment ···················································································································· 205
Default MDT-based transmission ··········································································································· 206
MDT switchover ····································································································································· 207
Layer 3 multicast in DCI scenarios········································································································· 208

iv
Layer 3 multicast in DCI multihoming scenarios ···················································································· 211
Configuring ingress replication MVXLAN ··················································· 212
Restrictions and guidelines: Multicast source location ··················································································· 212
Ingress replication MVXLAN tasks at a glance ······························································································ 212
Enabling IP multicast routing for a VPN instance··························································································· 212
Creating an MVXLAN ····································································································································· 213
Configuring a VSI interface as a distributed designated router interface ······················································· 213
Ingress replication MVXLAN configuration examples ···················································································· 214
Example: Configuring an ingress replication MVXLAN ·········································································· 214
Configuring MDT-based MVXLAN ····························································· 219
MDT-based MVXLAN tasks at a glance········································································································· 219
Restrictions: IGMP proxying configuration ····································································································· 219
Enabling IP multicast routing for a VPN instance··························································································· 220
Creating an MVXLAN ····································································································································· 220
Configuring a default group ···························································································································· 220
Specifying the MVXLAN source interface ······································································································ 221
Configuring MDT switchover parameters ······································································································· 222
Configuring a VSI interface as a distributed designated router interface ······················································· 222
Configuring an MVXLAN extranet RPF selection policy ················································································ 223
Configuring DRNI in MVXLAN ······················································································································· 225
Configuring DCI Layer 3 multicast ················································································································· 226
About this task ········································································································································ 226
Restrictions and guidelines ···················································································································· 226
Configuring an ED ·································································································································· 227
Configuring a VTEP ······························································································································· 227
Configuring an ED group for DCI Layer 3 multicast ······················································································· 228
Display and maintenance commands for MDT-based MVXLAN ··································································· 229
MDT-based MVXLAN configuration examples······························································································· 230
Example: Configuring intra-VPN MVXLAN Layer 3 multicast forwarding (IPv4 site network) ················ 230
Example: Configuring intra-VPN MVXLAN Layer 3 multicast forwarding (IPv6 site network) ················ 242
Example: Configuring MVXLAN extranet on the receiver VPN instance for symmetrically configured
extranet ·················································································································································· 254
Example: Configuring MVXLAN extranet on the receiver VPN instance for asymmetrically configured
extranet ·················································································································································· 268
Example: Configuring MVXLAN extranet with receivers on both VPNs and the public network ············ 281
Example: Configuring DRNI in MVXLAN with an Ethernet aggregate link as the IPL···························· 294
Example: Configuring DCI Layer 3 multicast without L3 VXLAN ID mapping ········································ 321
Example: Configuring DCI Layer 3 multicast with multiple L3 VXLAN IDs mapped to the same intermediate
L3 VXLAN ID ·········································································································································· 335
Example: Configuring DCI Layer 3 multicast with multiple L3 VXLAN IDs mapped to different intermediate
L3 VXLAN IDs ········································································································································ 358
Example: Configuring Layer 3 multicast without L3 VXLAN ID mapping in a DCI multihoming scenario
······························································································································································· 383
Document conventions and icons ······························································ 422
Conventions ··················································································································································· 422
Network topology icons ·································································································································· 423
Support and other resources ····································································· 424
Accessing Hewlett Packard Enterprise Support····························································································· 424
Accessing updates ········································································································································· 424
Websites ················································································································································ 425
Customer self repair ······························································································································· 425
Remote support ······································································································································ 425
Documentation feedback ······················································································································· 425
Index ·········································································································· 427

1
EVPN overview
Ethernet Virtual Private Network (EVPN) is a Layer 2 VPN technology that provides both Layer 2 and
Layer 3 connectivity between distant network sites across an IP or MPLS network. EVPN uses
MP-BGP in the control plane and Virtual eXtensible LAN (VXLAN) or MPLS in the data plane. EVPN
is typically used in data centers for multitenant services.
EVPN solutions
EVPN provides the EVPN VXLAN solution.
EVPN VXLAN
As shown in Figure 1, EVPN VXLAN uses the VXLAN technology for traffic forwarding in the data
plane. The transport edge devices assign VMs to different VXLANs, and then forward traffic at Layer
2 between sites for VMs by using VXLAN tunnels. The transport edge devices are VXLAN tunnel
endpoints (VTEPs). All EVPN VXLAN processing is performed on VTEPs
To provide Layer 3 connectivity between subnets of a tenant and between the EVPN VXLAN network
and external networks, you can deploy EVPN gateways.
For more information about EVPN VXLAN, see "Configuring EVPN VXLAN."
Figure 1 EVPN VXLAN network model
EVPN benefits
EVPN provides the following benefits:
•
Configuration automation—MP-BGP automates VTEP discovery, VXLAN tunnel
establishment, and VXLAN tunnel assignment to ease deployment.
•
Separation of the control plane and the data plane—EVPN uses MP-BGP to advertise host
reachability information in the control plane and uses VXLAN to forward traffic in the data plane.
•
Integrated routing and bridging (IRB)—MP-BGP advertises both Layer 2 and Layer 3 host
reachability information to provide optimal forwarding paths and minimize flooding in an EVPN
VXLAN network.
VXLAN tunnel
VTEP
Server Server
Site 1 Site 2
VM
VM
VM
VSI/VXLAN 10
VSI/VXLAN 20
VSI/VXLAN 30
VM
VM
VM
VSI/VXLAN 10
VSI/VXLAN 20
VSI/VXLAN 30
Transport
network
P
ES ES
VTEP

2
•
Point-to-point and point-to-multipoint connection—Layer 2 frames are transmitted
transparently across the IP transport network between sites after they are encapsulated into
VXLAN packets packets.
Layered transport network
As shown in Figure 2, typically the EVPN transport network uses a layered structure. On the
transport network, leaf nodes act as VTEPs or PEs to provide VXLAN services, and spine nodes
perform forwarding for VXLAN traffic based on the outer IP header. If all VTEPs and transport
network devices of an EVPN network belong to the same AS, the spine nodes can act as route
reflectors (RRs) to reflect routes between the VTEPs. In this scenario, the spine nodes advertise and
receive BGP EVPN routes, but do not perform VXLAN encapsulation and de-encapsulation.
Figure 2 Layered transport network
MP-BGP extension for EVPN
To support EVPN, MP-BGP introduces the EVPN subsequent address family under the L2VPN
address family and the following network layer reachability information (BGP EVPN routes):
•
Ethernet auto-discovery route—Advertises ES information in multihomed sites and
advertises service ID information in an EVPN VPWS network.
•
MAC/IP advertisement route—Advertises MAC reachability information and host route
information (host ARP or ND information).
•
Inclusive multicast Ethernet tag (IMET) route—Advertises VTEP and VXLAN mappings for
automating VTEP discovery, VXLAN tunnel establishment, and VXLAN tunnel assignment in an
EVPN VXLAN network. Advertises PE information for automating PE discovery and PW
establishment in an EVPN VPLS network.
•
Ethernet segment route—Advertises ES and VTEP mappings.
•
IP prefix advertisement route—Advertises BGP IPv4 or IPv6 unicast routes as IP prefixes.
•
Selective multicast Ethernet tag (SMET) route—Advertises IGMP multicast group
information among VTEPs in an EVPN network. A VTEP advertises an SMET route only when
receiving a membership report for an IGMP multicast group for the first time. The VTEP does
not advertise an SMET route if subsequent membership reports for the multicast group use the
same IGMP version as the first membership report.
VTEP
Server Server
Site 1 Site 2
Transport
network
VTEP
RR RR
Leaf
Spine

3
•
IGMP join synch route—Advertises IGMP membership reports among redundant VTEPs for
an ES.
•
IGMP leave synch route—Advertises IGMP leave group messages for withdrawal of IGMP
join synch routes among redundant VTEPs for an ES.
MP-BGP uses the route distinguisher (RD) field to differentiate BGP EVPN routes of different VSIs or
cross-connect groups and uses route targets to control the advertisement and acceptance of BGP
EVPN routes. MP-BGP supports the following types of route targets:
•
Export target—A VTEP or PE sets the export targets for BGP EVPN routes learned from the
local site before advertising them to remote VTEPs or PEs.
•
Import target—A VTEP or PE checks the export targets of BGP EVPN routes received from
remote VTEPs or PEs. The VTEP or PE imports the BGP EVPN routes only when their export
targets match the local import targets.
RD and route target selection of BGP EVPN
routes
As shown in Table 1, you can configure RDs and route targets for BGP EVPN routes in multiple
views.
Table 1 Supported views for RD and route target configuration
Item
Views
RD
• VSI EVPN instance view
• VPN instance view
• Public instance view
Route targets
• EVPN instance view
• VSI EVPN instance view
• VPN instance view
• VPN instance IPv4 address family view
• VPN instance IPv6 address family view
• VPN instance EVPN view
• Public instance view
• Public instance IPv4 address family view
• Public instance IPv6 address family view
• Public instance EVPN view
NOTE:
Route targets configured in VPN instance view apply to IPv4 VPN, IPv6 VPN, and
EVPN. Route targets configured in IPv4 address family view apply only to IPv4 VPN.
Route targets configured in IPv6 address family view apply only to IPv6 VPN. Route
targets configured in VPN instance EVPN view apply only to EVPN. Route targets
configured in IPv4 address family view, IPv6 address family view, or VPN instance
EVPN view take precedence over those in VPN instance view. The precedence order
for different views of a VPN instance also applies to the views of the public instance.
The device selects RDs and route targets for BGP EVPN routes by using the following rules:
•
IMET routes and MAC/IP advertisement routes that contain only MAC addresses—The
device uses the RD and route targets configured in VSI EVPN instance view when advertising
and accepting the routes.
•
MAC/IP advertisement routes that contain ARP or ND information—The device uses the
following settings when advertising the routes:
RD and export route targets configured in VSI EVPN instance view.

4
Export route targets configured for EVPN on a VPN instance or the public instance (VPN
instance view, EVPN view of a VPN instance or the public instance, and public instance
view).
The device uses the import route targets configured for EVPN on a VPN instance or the public
instance when accepting the routes.
•
IP prefix advertisement routes—The device uses the route targets configured for the IPv4 or
IPv6 address family on a VPN instance or the public instance when advertising and accepting
the routes.

5
EVPN VXLAN overview
EVPN VXLAN uses EVPN routes for automatic VXLAN tunnel establishment and assignment and
MAC reachability information advertisement in the control plane and uses VXLAN for forwarding in
the data plane.
Network model
As shown in Figure 3, EVPN uses the VXLAN technology for traffic forwarding in the data plane. The
transport edge devices assign user terminals to different VXLANs, and then forward traffic between
sites for user terminals by using VXLAN tunnels. The transport edge devices are VXLAN tunnel
endpoints (VTEPs).
Supported user terminals include PCs and VMs on servers.
NOTE:
This document uses VMs as examples to describe the mechanisms of EVPN. The mechanisms do
not differ between different kinds of user terminals.
A VTEP uses ESs, VSIs, and VXLAN tunnels to provide VXLAN services:
•
Ethernet segment (ES)—An ES is a link that connects a site to a VTEP. Each ES is uniquely
identified by an Ethernet segment identifier (ESI).
•
VSI—A virtual switch instance is a virtual Layer 2 switched domain. Each VSI provides
switching services only for one VXLAN. VSIs learn MAC addresses and forward frames
independently of one another. User terminals in different sites have Layer 2 connectivity if they
are in the same VXLAN. A VXLAN is identified by a 24-bit VXLAN ID which is also called the
virtual network identifier (VNI). A VXLAN corresponds to an EVPN instance.
•
VXLAN tunnel—Logical point-to-point tunnels between VTEPs over the transport network.
Each VXLAN tunnel can trunk multiple VXLANs.
All VXLAN processing is performed on VTEPs. The ingress VTEP encapsulates VXLAN traffic in the
VXLAN, outer UDP, and outer IP headers, and forwards the traffic through VXLAN tunnels. The
egress VTEP removes the VXLAN encapsulation and forwards the traffic to the destination.
Transport network devices (for example, the P device in Figure 3) forward VXLAN traffic only based
on the outer IP header of VXLAN packets.
Figure 3 EVPN network model
VXLAN tunnel
VTEP
Terminal
Terminal
Terminal
VSI/VXLAN 10
VSI/VXLAN 20
VSI/VXLAN 30
Terminal
Terminal
Terminal
VSI/VXLAN 10
VSI/VXLAN 20
VSI/VXLAN 30
Transport
network
P
ES ES
VTEP
Site 1 Site 2

6
Configuration automation
If EVPN is used for Layer 2 forwarding, VTEPs use the following BGP EVPN routes to discover
VTEP neighbors, establish VXLAN tunnels, and assign the tunnels to VXLANs:
•
IMET route—VTEPs advertise the VXLAN IDs they have through IMET routes. If two VTEPs
have the same VXLAN ID, they automatically establish a VXLAN tunnel and assign the tunnel
to the VXLAN.
•
MAC/IP advertisement route—VTEPs advertise local MAC addresses and VXLAN IDs
through MAC/IP advertisement routes. If two VTEPs have the same VXLAN ID, they
automatically establish a VXLAN tunnel and assign the tunnel to the VXLAN.
If EVPN is used for Layer 3 forwarding, VTEPs use the following BGP EVPN routes to discover
VTEP neighbors, establish VXLAN tunnels, and assign the tunnels to VXLANs:
•
IMET route—VTEPs advertise the VXLAN IDs they have through IMET routes. If two VTEPs
have the same VXLAN ID, they automatically establish a VXLAN tunnel and assign the tunnel
to the VXLAN.
•
MAC/IP advertisement route and IP prefix advertisement route—In the EVPN gateway
deployment, VTEPs advertise MAC/IP advertisement routes or IP prefix advertisement routes
with the export targets. When a VTEP receives a route, it compares the export targets of the
route with the local import targets. If the route targets match, the VTEP establishes a VXLAN
tunnel with the remote VTEP and associates the tunnel with the L3 VXLAN ID of the
corresponding VPN instance. For more information about the L3 VXLAN ID, see "Distributed
EVPN gateway deployment."
Assignment of traffic to VXLANs
Traffic from the local site to a remote site
The VTEP uses an Ethernet service instance to match customer traffic on a site-facing interface. The
VTEP assigns customer traffic to a VXLAN by mapping the Ethernet service instance to a VSI.
An Ethernet service instance is identical to an attachment circuit (AC) in L2VPN. An Ethernet service
instance matches a list of VLANs on a Layer 2 Ethernet interface by using a frame match criterion.
The frame match criterion specifies the characteristics of traffic from the VLANs, such as tagging
status and VLAN IDs.
As shown in Figure 4, Ethernet service instance 1 matches VLAN 2 and is mapped to VSI A (VXLAN
10). When a frame from VLAN 2 arrives, the VTEP assigns the frame to VXLAN 10, and looks up VSI
A's MAC address table for the outgoing interface.
Figure 4 Identifying traffic from the local site
Server
Service instance 1:
VLAN 2 VSI A
VXLAN 10
VLAN 2
VM 1
VM 2
VM 3
Service instance 2:
VLAN 3
Service instance 3:
VLAN 4
VLAN 3
VLAN 4
VSI B
VXLAN 20
VSI C
VXLAN 30
VTEP

7
Traffic from a remote site to the local site
When a VXLAN packet arrives at a VXLAN tunnel interface, the VTEP uses the VXLAN ID in the
packet to identify its VXLAN.
Layer 2 forwarding
MAC learning
The VTEP performs Layer 2 forwarding based on a VSI's MAC address table. The VTEP learns MAC
addresses by using the following methods:
•
Local MAC learning—The VTEP automatically learns the source MAC addresses of frames
sent from the local site. The outgoing interfaces of local MAC address entries are site-facing
interfaces on which the MAC addresses are learned.
•
Remote MAC learning—The VTEP uses MP-BGP to advertise local MAC reachability
information to remote sites and learn MAC reachability information from remote sites. The
outgoing interfaces of MAC address entries advertised from a remote site are VXLAN tunnel
interfaces.
Unicast
As shown in Figure 5, the VTEP performs typical Layer 2 forwarding for known unicast traffic within
the local site.
Figure 5 Intra-site unicast
As shown in Figure 6, the following process applies to a known unicast frame between sites:
1. The source VTEP encapsulates the Ethernet frame in the VXLAN/UDP/IP header.
In the outer IP header, the source IP address is the source VTEP's VXLAN tunnel source IP
address. The destination IP address is the VXLAN tunnel destination IP address.
2. The source VTEP forwards the encapsulated packet out of the outgoing VXLAN tunnel
interface found in the VSI's MAC address table.
3. The intermediate transport devices (P devices) forward the packet to the destination VTEP by
using the outer IP header.
VXLAN tunnel
VTEP 1 VTEP 2
Transport
network
P
Server 1
VM 1
VM 2
VM 3
Server 3
VM 7
VM 8
VM 9
MAC table on VTEP 1
VXLAN/VSI MAC Interface
VXLAN 10/VSI A MAC 1 Interface A, VLAN 2
VXLAN 10/VSI A MAC 4 Interface B, VLAN 3
Server 2
VM 4
VM 5
VM 6
Interface A
Interface B

8
4. The destination VTEP removes the headers on top of the inner Ethernet frame. It then performs
MAC address table lookup in the VXLAN's VSI to forward the frame out of the matching
outgoing interface.
Figure 6 Inter-site unicast
Flood
As shown in Figure 7, a VTEP floods a broadcast, multicast, or unknown unicast frame to all
site-facing interfaces and VXLAN tunnels in the VXLAN, except for the incoming interface. The
source VTEP replicates the flood frame, and then sends one replica to the destination IP address of
each VXLAN tunnel in the VXLAN. Each destination VTEP floods the inner Ethernet frame to all the
site-facing interfaces in the VXLAN. To avoid loops, the destination VTEPs do not flood the frame to
VXLAN tunnels.
VTEP 1 VTEP 2
Transport
network
P
Server 1
VM 1
VM 2
VM 3
Server 3
VM 7
VM 8
VM 9
MAC table on VTEP 1
VXLAN/VSI MAC Interface
VXLAN 10/VSI A MAC 1 Interface A, VLAN 2
VXLAN 10/VSI A MAC 7 Tunnel 1
Server 2
VM 4
VM 5
VM 6
Interface A
Interface B
MAC table on VTEP 2
VXLAN/VSI MAC Interface
VXLAN 10/VSI A MAC 1 Tunnel 1
VXLAN 10/VSI A MAC 7 Interface A, VLAN 3
Interface A
VXLAN tunnel 1

9
Figure 7 Forwarding of flood traffic
Centralized EVPN gateway deployment
IMPORTANT:
A centralized EVPN gateway can provide services only for IPv4 sites.
Centralized EVPN gateway deployment uses one VTEP to provide Layer 3 forwarding for VXLANs.
The VTEP uses virtual Layer 3 VSI interfaces as gateway interfaces for VXLANs. Typically, the
gateway-collocated VTEP connects to other VTEPs and the external network. To use this design,
make sure the gateway has sufficient bandwidth and processing capability.
As shown in Figure 8, a VTEP acts as a gateway for VMs in the VXLANs. The VTEP both terminates
the VXLANs and performs Layer 3 forwarding for the VMs. The network uses the following process
to forward Layer 3 traffic from a VM to the destination:
1. The VM sends an ARP request to obtain the MAC address of the VSI interface that acts as the
gateway, and then sends the Layer 3 traffic to the centralized EVPN gateway.
2. The local VTEP looks up the matching VSI's MAC address table and forwards the traffic to the
centralized EVPN gateway through a VXLAN tunnel.
3. The centralized EVPN gateway removes the VXLAN encapsulation and forwards the traffic at
Layer 3.
4. The centralized EVPN gateway forwards the replies sent by the destination node to the VM
based on the ARP entry for the VM.
VTEP 1 VTEP 2
Transport network
P
Server 1
VM 1
VM 2
VM 3
Server 3
VM 7
VM 8
VM 9
Server 2
VM 4
VM 5
VM 6
VXLAN tunnel
VXLAN tunnel
VTEP 3
VXLAN tunnel
Server 4
VM 10
VM 11
VM 12
Replicate and
encapsulate

10
Figure 8 Example of centralized EVPN gateway deployment
Distributed EVPN gateway deployment
IMPORTANT:
A distributed EVPN gateway can provide services for
IPv4 and IPv6 sites. This section uses IPv4
sites as examples to describe the Layer 3 forwarding process of EVPN networks.
The Layer 3
forwarding process does not differ between IPv4 and IPv6 sites.
About distributed EVPN gateway deployment
As shown in Figure 9, each site's VTEP acts as a gateway to perform Layer 3 forwarding for the
VXLANs of the local site. A VTEP acts as a border gateway to the Layer 3 network for the VXLANs.
VXLAN tunnel
VTEP 1 VTEP 2
Server Server
Site 1 Site 2
VM
VM
VM
VSI/VXLAN 10
VSI/VXLAN 20
VSI/VXLAN 30
VM
VM
VM
VSI/VXLAN 10
VSI/VXLAN 20
VSI/VXLAN 30
Transport
network
P
10.1.1.11
20.1.1.11
30.1.1.11
10.1.1.12
20.1.1.12
30.1.1.12
VXLAN tunnel
VXLAN tunnel
VTEP 3/Centralized EVPN gateway
VSI/VXLAN 10
VSI/VXLAN 20
VSI/VXLAN 30
VSI-interface10
10.1.1.1/24
VSI-interface20
20.1.1.1/24
VSI-interface30
30.1.1.1/24
L3 network

11
Figure 9 Distributed EVPN gateway placement design
A distributed EVPN gateway supports the following traffic forwarding modes:
•
Asymmetric IRB—The ingress gateway performs Layer 2 and Layer 3 lookups and the egress
gateway performs only Layer 2 forwarding.
•
Symmetric IRB—Both the ingress and egress gateways perform Layer 2 and Layer 3 lookups.
Symmetric IRB
Basic concepts
Symmetric IRB introduces the following concepts:
•
L3 VXLAN ID—Also called L3 VNI. An L3 VXLAN ID identifies the traffic of a routing domain
where devices have Layer 3 reachability. An L3 VXLAN ID is associated with one VPN instance.
Distributed EVPN gateways use VPN instances to isolate traffic of different services on VXLAN
tunnel interfaces.
•
Router MAC address—Each distributed EVPN gateway has a unique router MAC address
used for inter-gateway forwarding. The MAC addresses in the inner Ethernet header of VXLAN
packets are router MAC addresses of distributed EVPN gateways.
VSI interfaces
As shown in Figure 10, each distributed EVPN gateway has the following types of VSI interfaces:
•
VSI interface as a gateway interface of a VXLAN—The VSI interface acts as the gateway
interface for VMs in a VXLAN. The VSI interface is associated with a VSI and a VPN instance.
On different distributed EVPN gateways, the VSI interface of a VXLAN use the same IP address
to provide services.
•
VSI interface associated with an L3 VXLAN ID—The VSI interface is associated with a VPN
instance and assigned an L3 VXLAN ID. VSI interfaces associated with the same VPN instance
share an L3 VXLAN ID.
A border gateway only has VSI interfaces that are associated with an L3 VXLAN ID.
VXLAN tunnel
VXLAN tunnel
VTEP
Server
Site 1
L3 network
VXLAN tunnel VXLAN tunnel
Server
Site 2
Server
Site 3
Server
Site 4
Server
Site 5
Server
Site 6
VTEP/Distributed
EVPN gateway
Border gateway
VTEP/Distributed
EVPN gateway
VTEP/Distributed
EVPN gateway

12
Figure 10 Example of distributed EVPN gateway deployment
Layer 3 forwarding entry learning
A distributed EVPN gateway forwards Layer 3 traffic based on FIB entries generated from BGP
EVPN routes and ARP information.
A VTEP advertises an external route imported in the EVPN address family through MP-BGP. A
remote VTEP adds the route to the FIB table of a VPN instance based on the L3 VXLAN ID carried in
the route. In the FIB entry, the outgoing interface is a VXLAN tunnel interface, and the next hop is the
peer VTEP address in the NEXT_HOP attribute of the route.
A VTEP has the following types of ARP information:
•
Local ARP information—ARP information of VMs in the local site. The VTEP snoops GARP
packets, RARP packets, and ARP requests for the gateway MAC address to learn the ARP
information of the senders and generates ARP entries and FIB entries. In an ARP or FIB entry,
the outgoing interface is the site-facing interface where the packet is received, and the VPN
instance is the instance associated with the corresponding VSI interface.
•
Remote ARP information—ARP information of VMs in remote sites. Each VTEP uses
MP-BGP to advertise its local ARP information with L3 VXLAN IDs in routes to remote sites. A
VTEP generates only FIB entries for the remote ARP information. A FIB entry contains the
following information:
Outgoing interface: VSI interface associated with the L3 VXLAN ID.
Next hop: Peer VTEP address in the NEXT_HOP attribute of the route.
VPN instance: VPN instance associated with the L3 VXLAN ID.
The VTEP then creates an ARP entry for the next hop in the FIB entry.
Traffic forwarding
A distributed EVPN gateway can work in one of the following mode:
VXLAN tunnel
GW 1 GW 2
Server Server
Site 1 Site 2
VM 1
VM 2
VSI/VXLAN 10
VSI/VXLAN 20
VM 4
VM 5
VSI/VXLAN 10
VSI/VXLAN 20
P
10.1.1.11
20.1.1.11
10.1.1.12
20.1.1.12
VXLAN tunnel
VXLAN tunnel
Border
gateway
L3 network
VSI-interface10
10.1.1.1/24
VPN instance: vpna
VSI-interface20
20.1.1.1/24
VPN instance: vpna
VSI-interface1
VPN instance: vpna
L3VNI: 1000
VSI-interface1
VPN instance: vpna
L3VNI: 1000

13
•
Switching and routing mode—Forwards Layer 2 traffic based on the MAC address table and
forwards Layer 3 traffic based on the FIB table. In this mode, you need to enable ARP flood
suppression on the distributed EVPN gateway to reduce flooding.
•
Routing mode— Forwards both Layer 2 and Layer 3 traffic based on the FIB table. In this
mode, you need to enable local proxy ARP on the distributed EVPN gateway.
For more information about MAC address table-based Layer 2 forwarding, see "Unicast."
Figure 11 shows the intra-site Layer 3 forwarding process.
1. The source VM sends an ARP request to obtain the MAC address of the destination VM.
2. The gateway replies to the source VM with the MAC address of the VSI interface associated
with the source VM's VSI.
3. The source VM sends a Layer 3 packet to the gateway.
4. The gateway looks up the FIB table of the VPN instance associated with the source VM's VSI
and finds the matching outgoing site-facing interface.
5. The gateway processes the Ethernet header of the Layer 3 packet as follows:
Replaces the destination MAC address with the destination VM's MAC address.
Replaces the source MAC address with the VSI interface's MAC address.
6. The gateway forwards the Layer 3 packet to the destination VM.
Figure 11 Intra-site Layer 3 forwarding
Figure 12 shows the inter-site Layer 3 forwarding process.
1. The source VM sends an ARP request to obtain the MAC address of the destination VM.
2. The gateway replies to the source VM with the MAC address of the VSI interface associated
with the source VM's VSI.
3. The source VM sends a Layer 3 packet to the gateway.
4. The gateway looks up the FIB table of the VPN instance associated with the source VM's VSI
and finds the matching outgoing VSI interface.
5. The gateway processes the Ethernet header of the Layer 3 packet as follows:
Replaces the destination MAC address with the destination gateway's router MAC address.
Replaces the source MAC address with its own router MAC address.
6. The gateway adds VXLAN encapsulation to the Layer 3 packet and forwards the packet to the
destination gateway. The encapsulated VXLAN ID is the L3 VXLAN ID of the corresponding
VPN instance.
7. The destination gateway identifies the VPN instance of the packet based on the L3 VXLAN ID
and removes the VXLAN encapsulation. Then the gateway forwards the packet based on the
matching ARP entry.
GW 1
DATA
Server 1
VM 1
IP 1
MAC 1
Server 2
VM 2
IP 2
MAC 2
GW IP
GW MAC (VSI interface MAC)
SIP: IP 1
DIP: IP 2
SMAC: MAC 1
DMAC: GW MAC
DATA
SIP: IP 1
DIP: IP 2
SMAC: GW MAC
DMAC: MAC 2

14
Figure 12 Inter-site Layer 3 forwarding
Communication between private and public networks
A distributed EVPN gateway uses the public instance to perform Layer 3 forwarding for the public
network and to enable communication between private and public networks. The public instance is
similar to a VPN instance. A distributed EVPN gateway processes traffic of the public instance in the
same way it does for a VPN instance. For the public instance to work correctly, you must configure
an RD, an L3 VXLAN ID, and route targets for it. If a VSI interface is not associated with any VPN
instance, the VSI interface belongs to the public instance.
Asymmetric IRB
VSI interfaces
Asymmetric IRB uses the same distributed EVPN gateway deployment as symmetric IRB.
As shown in Figure 10, each distributed EVPN gateway has the following types of VSI interfaces:
•
VSI interface as a gateway interface of a VXLAN—The VSI interface is associated with a VSI
and a VPN instance. On different distributed EVPN gateways, the VSI interface of a VXLAN
must use different IP addresses to provide services.
•
VSI interface associated with an L3 VXLAN ID—The VSI interface acts as the gateway for
VMs in a VXLAN to communicate with the external network through the border gateway. The
VSI interface is associated with a VPN instance and assigned an L3 VXLAN ID. VSI interfaces
associated with the same VPN instance share an L3 VXLAN ID.
A border gateway only has VSI interfaces that are associated with an L3 VXLAN ID.
Layer 3 forwarding
Asymmetric IRB supports only Layer 3 forwarding in the same VXLAN on distributed EVPN
gateways.
After a distributed EVPN gateway learns ARP information about local VMs, it advertises the
information to other distributed EVPN gateways through MAC/IP advertisement routes. Other
distributed EVPN gateways generate FIB entries based on the advertised ARP information.
As shown in Figure 13, VM 1 and VM 2 belong to VXLAN 10 and they can reach each other at Layer
3 through the distributed EVPN gateways. The distributed EVPN gateways use the following process
to perform Layer 3 forwarding in asymmetric IRB mode when VM 1 sends a packet to VM 2:
GW 1 P GW 2
DATA
Transport
network
Server 1
VM 1
IP 1
MAC 1
Server 2
VM 2
IP 2
MAC 2
GW IP
GW MAC (VSI interface MAC)
GW MAC 1 (Router MAC of GW 1)
VTEP IP 1
L3VNI 100
GW IP
GW MAC (VSI interface MAC)
GW MAC 2 (Router MAC of GW 2)
VTEP IP 2
L3VNI 100
SIP: IP 1
DIP: IP 2
SMAC: MAC 1
DMAC: GW MAC
DATA
SIP: IP 1
DIP: IP 2
SMAC: GW MAC 1
DMAC: GW MAC 2
VNI: 100
SIP: VTEP IP 1
DIP: VTEP IP 2
DATA
SIP: IP 1
DIP: IP 2
SMAC: GW MAC
DMAC: MAC 2
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
-
 1
1
-
 2
2
-
 3
3
-
 4
4
-
 5
5
-
 6
6
-
 7
7
-
 8
8
-
 9
9
-
 10
10
-
 11
11
-
 12
12
-
 13
13
-
 14
14
-
 15
15
-
 16
16
-
 17
17
-
 18
18
-
 19
19
-
 20
20
-
 21
21
-
 22
22
-
 23
23
-
 24
24
-
 25
25
-
 26
26
-
 27
27
-
 28
28
-
 29
29
-
 30
30
-
 31
31
-
 32
32
-
 33
33
-
 34
34
-
 35
35
-
 36
36
-
 37
37
-
 38
38
-
 39
39
-
 40
40
-
 41
41
-
 42
42
-
 43
43
-
 44
44
-
 45
45
-
 46
46
-
 47
47
-
 48
48
-
 49
49
-
 50
50
-
 51
51
-
 52
52
-
 53
53
-
 54
54
-
 55
55
-
 56
56
-
 57
57
-
 58
58
-
 59
59
-
 60
60
-
 61
61
-
 62
62
-
 63
63
-
 64
64
-
 65
65
-
 66
66
-
 67
67
-
 68
68
-
 69
69
-
 70
70
-
 71
71
-
 72
72
-
 73
73
-
 74
74
-
 75
75
-
 76
76
-
 77
77
-
 78
78
-
 79
79
-
 80
80
-
 81
81
-
 82
82
-
 83
83
-
 84
84
-
 85
85
-
 86
86
-
 87
87
-
 88
88
-
 89
89
-
 90
90
-
 91
91
-
 92
92
-
 93
93
-
 94
94
-
 95
95
-
 96
96
-
 97
97
-
 98
98
-
 99
99
-
 100
100
-
 101
101
-
 102
102
-
 103
103
-
 104
104
-
 105
105
-
 106
106
-
 107
107
-
 108
108
-
 109
109
-
 110
110
-
 111
111
-
 112
112
-
 113
113
-
 114
114
-
 115
115
-
 116
116
-
 117
117
-
 118
118
-
 119
119
-
 120
120
-
 121
121
-
 122
122
-
 123
123
-
 124
124
-
 125
125
-
 126
126
-
 127
127
-
 128
128
-
 129
129
-
 130
130
-
 131
131
-
 132
132
-
 133
133
-
 134
134
-
 135
135
-
 136
136
-
 137
137
-
 138
138
-
 139
139
-
 140
140
-
 141
141
-
 142
142
-
 143
143
-
 144
144
-
 145
145
-
 146
146
-
 147
147
-
 148
148
-
 149
149
-
 150
150
-
 151
151
-
 152
152
-
 153
153
-
 154
154
-
 155
155
-
 156
156
-
 157
157
-
 158
158
-
 159
159
-
 160
160
-
 161
161
-
 162
162
-
 163
163
-
 164
164
-
 165
165
-
 166
166
-
 167
167
-
 168
168
-
 169
169
-
 170
170
-
 171
171
-
 172
172
-
 173
173
-
 174
174
-
 175
175
-
 176
176
-
 177
177
-
 178
178
-
 179
179
-
 180
180
-
 181
181
-
 182
182
-
 183
183
-
 184
184
-
 185
185
-
 186
186
-
 187
187
-
 188
188
-
 189
189
-
 190
190
-
 191
191
-
 192
192
-
 193
193
-
 194
194
-
 195
195
-
 196
196
-
 197
197
-
 198
198
-
 199
199
-
 200
200
-
 201
201
-
 202
202
-
 203
203
-
 204
204
-
 205
205
-
 206
206
-
 207
207
-
 208
208
-
 209
209
-
 210
210
-
 211
211
-
 212
212
-
 213
213
-
 214
214
-
 215
215
-
 216
216
-
 217
217
-
 218
218
-
 219
219
-
 220
220
-
 221
221
-
 222
222
-
 223
223
-
 224
224
-
 225
225
-
 226
226
-
 227
227
-
 228
228
-
 229
229
-
 230
230
-
 231
231
-
 232
232
-
 233
233
-
 234
234
-
 235
235
-
 236
236
-
 237
237
-
 238
238
-
 239
239
-
 240
240
-
 241
241
-
 242
242
-
 243
243
-
 244
244
-
 245
245
-
 246
246
-
 247
247
-
 248
248
-
 249
249
-
 250
250
-
 251
251
-
 252
252
-
 253
253
-
 254
254
-
 255
255
-
 256
256
-
 257
257
-
 258
258
-
 259
259
-
 260
260
-
 261
261
-
 262
262
-
 263
263
-
 264
264
-
 265
265
-
 266
266
-
 267
267
-
 268
268
-
 269
269
-
 270
270
-
 271
271
-
 272
272
-
 273
273
-
 274
274
-
 275
275
-
 276
276
-
 277
277
-
 278
278
-
 279
279
-
 280
280
-
 281
281
-
 282
282
-
 283
283
-
 284
284
-
 285
285
-
 286
286
-
 287
287
-
 288
288
-
 289
289
-
 290
290
-
 291
291
-
 292
292
-
 293
293
-
 294
294
-
 295
295
-
 296
296
-
 297
297
-
 298
298
-
 299
299
-
 300
300
-
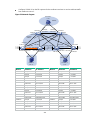 301
301
-
 302
302
-
 303
303
-
 304
304
-
 305
305
-
 306
306
-
 307
307
-
 308
308
-
 309
309
-
 310
310
-
 311
311
-
 312
312
-
 313
313
-
 314
314
-
 315
315
-
 316
316
-
 317
317
-
 318
318
-
 319
319
-
 320
320
-
 321
321
-
 322
322
-
 323
323
-
 324
324
-
 325
325
-
 326
326
-
 327
327
-
 328
328
-
 329
329
-
 330
330
-
 331
331
-
 332
332
-
 333
333
-
 334
334
-
 335
335
-
 336
336
-
 337
337
-
 338
338
-
 339
339
-
 340
340
-
 341
341
-
 342
342
-
 343
343
-
 344
344
-
 345
345
-
 346
346
-
 347
347
-
 348
348
-
 349
349
-
 350
350
-
 351
351
-
 352
352
-
 353
353
-
 354
354
-
 355
355
-
 356
356
-
 357
357
-
 358
358
-
 359
359
-
 360
360
-
 361
361
-
 362
362
-
 363
363
-
 364
364
-
 365
365
-
 366
366
-
 367
367
-
 368
368
-
 369
369
-
 370
370
-
 371
371
-
 372
372
-
 373
373
-
 374
374
-
 375
375
-
 376
376
-
 377
377
-
 378
378
-
 379
379
-
 380
380
-
 381
381
-
 382
382
-
 383
383
-
 384
384
-
 385
385
-
 386
386
-
 387
387
-
 388
388
-
 389
389
-
 390
390
-
 391
391
-
 392
392
-
 393
393
-
 394
394
-
 395
395
-
 396
396
-
 397
397
-
 398
398
-
 399
399
-
 400
400
-
 401
401
-
 402
402
-
 403
403
-
 404
404
-
 405
405
-
 406
406
-
 407
407
-
 408
408
-
 409
409
-
 410
410
-
 411
411
-
 412
412
-
 413
413
-
 414
414
-
 415
415
-
 416
416
-
 417
417
-
 418
418
-
 419
419
-
 420
420
-
 421
421
-
 422
422
-
 423
423
-
 424
424
-
 425
425
-
 426
426
-
 427
427
-
 428
428
-
 429
429
-
 430
430
-
 431
431
-
 432
432
-
 433
433
-
 434
434
-
 435
435
-
 436
436
-
 437
437
-
 438
438
-
 439
439
-
 440
440
-
 441
441
-
 442
442
-
 443
443
-
 444
444
-
 445
445
-
 446
446
-
 447
447
Aruba FlexFabric 5940 Switch Series EVPN Configuration Guide
- Category
- Networking
- Type
- Configuration Guide
Ask a question and I''ll find the answer in the document
Finding information in a document is now easier with AI
Related papers
-
Aruba EVPN Configuration Guide
-
Aruba R9F19A Configuration Guide
-
Aruba JH103A Reference guide
-
Aruba EVPN User guide
-
Aruba FlexFabric 5940 Switch Series EVPN Reference guide
-
Aruba JL852AAE Configuration Guide
-
Aruba JL852AAE Configuration Guide
-
Aruba JH691A User guide
-
Aruba DRNI+EVPN Configuration Guide
-
Aruba JH348A Configuration Guide
Other documents
-
Dell SmartFabric OS10 Documentation Owner's manual
-
Dell SmartFabric OS10 Documentation Owner's manual
-
Dell PowerSwitch S4248FB-ON /S4248FBL-ON Owner's manual
-
Dell PowerSwitch S4248FB-ON /S4248FBL-ON Owner's manual
-
Dell SmartFabric OS10 Documentation Owner's manual
-
Cisco IOS XR Software Release 6.4 Configuration Guide
-
Dell PowerSwitch S4248FB-ON /S4248FBL-ON Owner's manual
-
Juniper Contrail Networking User guide
-
Dell VxRail P570 Owner's manual
-
Dell PowerSwitch S4248FB-ON /S4248FBL-ON User guide






























































































































































































































































































































































































































































