Hitachi VSP G1500 User And Reference Manual
- Type
- User And Reference Manual

Command Control Interface
User and Reference Guide
Hitachi Virtual Storage Platform G1000 and G1500
Hitachi Virtual Storage Platform F1500
Hitachi Virtual Storage Platform G200, G400, G600, G800
Hitachi Virtual Storage Platform F400, F600, F800
Hitachi Virtual Storage
Hitachi PlatformUnified Storage VM
Hitachi Universal Storage Platform V/VM
MK-90RD7010-32
May 2017

© 2010, 2017 Hitachi, Ltd. All rights reserved.
No part of this publication may be reproduced or transmitted in any form or by any means,
electronic or mechanical, including copying and recording, or stored in a database or retrieval
system for any purpose without the express written permission of Hitachi, Ltd., or Hitachi Data
Systems Corporation (collectively “Hitachi”). Licensee may make copies of the Materials provided
that any such copy is: (i) created as an essential step in utilization of the Software as licensed and
is used in no other manner; or (ii) used for archival purposes. Licensee may not make any other
copies of the Materials. “Materials” mean text, data, photographs, graphics, audio, video and
documents.
Hitachi reserves the right to make changes to this Material at any time without notice and assumes
no responsibility for its use. The Materials contain the most current information available at the time
of publication.
Some of the features described in the Materials might not be currently available. Refer to the most
recent product announcement for information about feature and product availability, or contact
Hitachi Data Systems Corporation at
https://support.hds.com/en_us/contact-us.html.
Notice: Hitachi products and services can be ordered only under the terms and conditions of the
applicable Hitachi Data Systems Corporation agreements. The use of Hitachi products is governed
by the terms of your agreements with Hitachi Data Systems Corporation.
By using this software, you agree that you are responsible for:
1) Acquiring the relevant consents as may be required under local privacy laws or otherwise from
authorized employees and other individuals to access relevant data; and
2) Verifying that data continues to be held, retrieved, deleted, or otherwise processed in accordance
with relevant laws.
Notice on Export Controls. The technical data and technology inherent in this Document may be
subject to U.S. export control laws, including the U.S. Export Administration Act and its associated
regulations, and may be subject to export or import regulations in other countries. Reader agrees to
comply strictly with all such regulations and acknowledges that Reader has the responsibility to
obtain licenses to export, re-export, or import the Document and any Compliant Products.
Hitachi is a registered trademark of Hitachi, Ltd., in the United States and other countries.
AIX, AS/400e, DB2, Domino, DS6000, DS8000, Enterprise Storage Server, eServer, FICON,
FlashCopy, IBM, Lotus, MVS, OS/390, PowerPC, RS/6000, S/390, System z9, System z10, Tivoli,
z/OS, z9, z10, z13, z/VM, and z/VSE are registered trademarks or trademarks of International
Business Machines Corporation.
Active Directory, ActiveX, Bing, Excel, Hyper-V, Internet Explorer, the Internet Explorer logo,
Microsoft, the Microsoft Corporate Logo, MS-DOS, Outlook, PowerPoint, SharePoint, Silverlight,
SmartScreen, SQL Server, Visual Basic, Visual C++, Visual Studio, Windows, the Windows logo,
Windows Azure, Windows PowerShell, Windows Server, the Windows start button, and Windows
Vista are registered trademarks or trademarks of Microsoft Corporation. Microsoft product screen
shots are reprinted with permission from Microsoft Corporation.
All other trademarks, service marks, and company names in this document or website are
properties of their respective owners.
ii
Command Control Interface User and Reference Guide

Contents
Preface.................................................................................................. xi
Intended audience....................................................................................................xii
Product version........................................................................................................ xii
Release notes...........................................................................................................xii
Changes in this revision............................................................................................ xii
Referenced documents.............................................................................................xiii
Document conventions.............................................................................................xiv
Convention for storage capacity values......................................................................xvi
Accessing product documentation............................................................................ xvii
Getting help........................................................................................................... xvii
Comments..............................................................................................................xvii
1 Overview..............................................................................................1-1
About Command Control Interface........................................................................... 1-2
CCI functions..........................................................................................................1-2
CCI functions matrix......................................................................................... 1-2
Provisioning functions....................................................................................... 1-3
Asynchronous command processing...................................................................1-3
Command execution modes...............................................................................1-4
Precheck function............................................................................................. 1-4
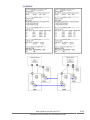
Command execution by the in-band and out-of-band methods.............................1-5
User authentication mode................................................................................. 1-8
LDEV nickname function....................................................................................1-8
LDEV grouping function.................................................................................... 1-8
Resource group function................................................................................... 1-9
Resource locking function..................................................................................1-9
CCI functions available on all RAID storage systems..................................................1-9
In-system replication........................................................................................ 1-9
Remote replication............................................................................................1-9
Data protection...............................................................................................1-10
2 CCI software environment.....................................................................2-1
Overview of the CCI software environment...............................................................2-2
CCI components on the RAID storage system........................................................... 2-2
Command device..............................................................................................2-2
iii
Command Control Interface User and Reference Guide

Command device guarding.......................................................................2-3
Alternate command device function.......................................................... 2-5
Remote command device.........................................................................2-6
CCI and the SCSI command interface.................................................................2-7
Command competition.............................................................................2-8
Command flow........................................................................................2-8
Issuing commands for LDEVs within a LUSE device....................................2-9
CCI instance components on the host server.............................................................2-9
HORCM operational environment....................................................................... 2-9
CCI instance configurations............................................................................. 2-10
Host machines that can be paired.................................................................... 2-12
Configuration definition file..............................................................................2-13
Configuration definition file settings................................................................. 2-16
HORCM_MON........................................................................................2-17
HORCM_CMD (in-band method)............................................................. 2-17
HORCM_CMD (out-of-band method)....................................................... 2-21
HORCM_DEV.........................................................................................2-23
HORCM_INST........................................................................................2-25
HORCM_LDEV....................................................................................... 2-26
HORCM_LDEVG.....................................................................................2-27
HORCM_INSTP......................................................................................2-28
HORCM_ALLOW_INST........................................................................... 2-28
Correspondence of the configuration definition file for cascading volume and mirror
descriptors..................................................................................................... 2-28
Correspondence of configuration file and mirror descriptors......................2-29
Cascading connection and configuration files...........................................2-30
ShadowImage.......................................................................................2-31
Cascading connections for TrueCopy and ShadowImage.......................... 2-33
CCI software files..................................................................................................2-35
CCI files supplied with the software..................................................................2-36
CCI files for UNIX-based systems............................................................2-36
CCI files for Windows-based systems...................................................... 2-37
CCI files for OpenVMS-based systems..................................................... 2-39
CCI log and trace files........................................................................................... 2-40
CCI log files....................................................................................................2-40
CCI trace files.................................................................................................2-43
CCI trace control command............................................................................. 2-43
Command logging for audit............................................................................. 2-43
Logging other than raidcom command.................................................... 2-43
Logging raidcom command.................................................................... 2-46
User-created files..................................................................................................2-49
User environment variable..................................................................................... 2-49
3 CCI functions........................................................................................3-1
System configuration using CCI............................................................................... 3-2
In-band system configurations and out-of-band system configurations................. 3-2
System configuration for connecting to a CCI server connected by the in-band
method using the out-of-band method............................................................... 3-5
Connecting to CCI server already connected by In-Band method using Out-of-Band
method.................................................................................................................. 3-5
User authentication.................................................................................................3-8
Command operation authority and user authentication.............................................. 3-9
iv
Command Control Interface User and Reference Guide

Controlling User Role........................................................................................ 3-9
Controlling user resources............................................................................... 3-10
Commands executed depending on operation authorities...................................3-13
Relation between resource groups and command operations....................................3-21
Resource lock function.......................................................................................... 3-24
Command execution modes...................................................................................3-25
Overview........................................................................................................3-25
Context check.................................................................................................3-26
How to check........................................................................................ 3-27
Details of check contents....................................................................... 3-27
Configuration check........................................................................................ 3-33
Resource location and parameter........................................................................... 3-34
MP blade location and parameter..................................................................... 3-34
LDEV grouping function.........................................................................................3-35
Overview........................................................................................................3-35
Device group definition methods......................................................................3-38
Read operations and command device settings................................................. 3-38
Define device group........................................................................................3-39
Device group creation............................................................................3-40
LDEV addition to device group................................................................3-41
LDEV deletion from device group............................................................3-41
Device group deletion............................................................................ 3-42
Copy group function........................................................................................3-43
Copy group creation.............................................................................. 3-45
LDEV addition to a copy group............................................................... 3-45
LDEV deletion from copy group.............................................................. 3-46
Copy group deletion.............................................................................. 3-47
Pair operation by specifying a copy group............................................... 3-47
Pair operations with mainframe volumes.................................................................3-49
Using "dummy" LUs for mainframe LDEVs........................................................ 3-49
Pair status and access permission for mainframe LDEVs.................................... 3-50
Operational differences for multiplatform volumes.............................................3-52
Operational differences for replication commands............................................. 3-53
Global storage virtualization function...................................................................... 3-54
System configuration example with the global storage virtualization function...... 3-54
Using CCI with the global storage virtualization function.................................... 3-55
Configuration definition file settings with global storage virtualization................. 3-55
Example of the configuration definition files when specifying a virtual storage
machine by HORCM_CMD................................................................................3-57
Specifying a virtual storage machine to HORCM_VCMD......................................3-59
Command operations to the virtual storage machine................................3-59
Operation target for raidcom commands when specifying the virtual storage
machine in HORCM_VCMD..................................................................... 3-61
raidcom commands for volumes that belong to virtual storage machine for
HORCM_CMD........................................................................................ 3-68
4 Starting up CCI.....................................................................................4-1
Starting up on UNIX systems................................................................................... 4-2
Starting up on Windows systems..............................................................................4-3
Starting up on OpenVMS systems.............................................................................4-4
Starting CCI as a service (Windows systems)............................................................ 4-6
v
Command Control Interface User and Reference Guide

5 Provisioning operations with CCI............................................................5-1
About provisioning operations..................................................................................5-2
Overview of the configuration setting command..................................................5-2
Synchronous command processing........................................................... 5-3
Asynchronous command processing..........................................................5-3
Errors during asynchronous command processing......................................5-3
Workflow for executing asynchronous commands...................................... 5-4
Asynchronous commands.........................................................................5-4
Help on configuration setting commands............................................................5-6
LDEV nickname function....................................................................................5-6
Available provisioning operations............................................................................. 5-6
Provisioning operations that can be performed on device groups..............................5-13
Operation method...........................................................................................5-14
Workflow for performing provisioning operations.....................................................5-15
Resource group operations.................................................................................... 5-16
Creating resource groups................................................................................ 5-16
Deleting resource groups.................................................................................5-16
Allocating resources to other resource groups...................................................5-17
Execution example..........................................................................................5-18
Internal volume operations.................................................................................... 5-18
Creating internal volumes (open-systems)........................................................ 5-18
Script examples (open systems).......................................................................5-20
Creating internal volumes (Mainframe volume)................................................. 5-22
Script examples.....................................................................................5-23
Script examples.............................................................................................. 5-25
Virtual volume (Dynamic Provisioning) operations....................................................5-26
Creating virtual volumes (Dynamic Provisioning)............................................... 5-26
Script examples.............................................................................................. 5-28
Deleting a virtual volume for which capacity saving is enabled........................... 5-31
Using the -operation initialize_capacity_saving option of the
raidcom delete ldev command to delete a virtual volume.................5-31
Deleting a virtual volume by blocking, initializing, and then deleting the
volume................................................................................................. 5-32
Virtual volume (Dynamic Provisioning for Mainframe) operations.............................. 5-33
Creating virtual volumes (Dynamic Provisioning for Mainframe)..........................5-33
Script examples.............................................................................................. 5-34
Virtual volume (Dynamic Tiering) operations........................................................... 5-36
Operational flow............................................................................................. 5-36
Creating virtual volumes (Dynamic Tiering).......................................................5-38
Script examples.............................................................................................. 5-40
Configuring iSCSI virtual ports............................................................................... 5-43
Setting an iSCSI virtual port.............................................................................5-44
Deleting an iSCSI virtual port...........................................................................5-44
External volume operations....................................................................................5-45
Creating external volumes (Fibre Channel)........................................................5-45
Creating external volumes (iSCSI)....................................................................5-47
Script Examples.............................................................................................. 5-50
Virtual Partition Manager operations.......................................................................5-53
Performing Virtual Partition Manager operations................................................5-53
Displaying CLPR information............................................................................ 5-54
Migrating parity groups in a CLPR.................................................................... 5-54
Displaying parity group information........................................................ 5-54
vi
Command Control Interface User and Reference Guide

Moving parity groups............................................................................. 5-54
Checking result of CLPR transfer.............................................................5-55
Server Priority Manager operations.........................................................................5-55
Configuring Server Priority Manager by specifying ports and WWNs of HBAs....... 5-56
Controlling the priority of I/O operations in storage systems on servers.....5-56
Using and managing Server Priority Manager...........................................5-57
Setting SPM names for WWNs and registering them to the SPM group...... 5-58
Configuring Server Priority Manager by specifying ports and WWNs of HBAs
............................................................................................................5-58
Cautions about using Server Priority Manager..........................................5-63
Cautions when using host groups after registering them in SPM groups (VSP
only).................................................................................................... 5-65
Configuring Server Priority Manager by specifying LDEVs and WWNs or iSCSI names
of HBAs..........................................................................................................5-66
Virtual storage machine operations.........................................................................5-68
Creating host groups in a virtual storage machine............................................. 5-68
Adding LDEVs to a virtual storage machine.......................................................5-69
Removing the virtual storage machine..............................................................5-70
6 Data replication operations with CCI...................................................... 6-1
About data replication operations.............................................................................6-2
Features of paired volumes......................................................................................6-2
Using CCI with ShadowImage and TrueCopy............................................................ 6-3
Using CCI with Thin Image......................................................................................6-4
Using CCI with global-active device..........................................................................6-5
ShadowImage operations........................................................................................ 6-5
ShadowImage duplicated mirroring....................................................................6-6
ShadowImage cascading pairs...........................................................................6-7
Restrictions for ShadowImage cascading volumes......................................6-8
Restriction for TrueCopy/ShadowImage cascading volumes........................6-9
TrueCopy operations...............................................................................................6-9
TrueCopy takeover commands.........................................................................6-10
Takeover-switch function....................................................................... 6-12
Swap-takeover function......................................................................... 6-13
SVOL-takeover function......................................................................... 6-14
PVOL-takeover function......................................................................... 6-15
TrueCopy remote commands........................................................................... 6-15
TrueCopy local commands...............................................................................6-17
TrueCopy, ShadowImage, and Universal Replicator operations................................. 6-17
TrueCopy/ShadowImage volumes.................................................................... 6-17
TrueCopy/ShadowImage/Universal Replicator pair status...................................6-18
TrueCopy Async, TrueCopy, Universal Replicator, and global-active device volumes
..................................................................................................................... 6-24
Sidefile cache for TrueCopy Async.......................................................... 6-27
TrueCopy Async transition states and sidefile control............................... 6-27
TrueCopy Async/Universal Replicator error state......................................6-29
TrueCopy/TrueCopy Async and Universal Replicator/global-active device fence level
settings..........................................................................................................6-30
Setting the fence level........................................................................... 6-32
Copy-on-Write Snapshot operations........................................................................6-33
Copy-on-Write Snapshot volumes.....................................................................6-33
Pair operations and commands for Copy-on-Write Snapshot and Thin Image ..... 6-34
vii
Command Control Interface User and Reference Guide

Creating a Copy-on-Write Snapshot pair........................................................... 6-34
Copy-on-Write Snapshot pair status................................................................. 6-35
Pair status relationship to Copy-on-Write Snapshot commands...........................6-36
Controlling Volume Migration................................................................................. 6-37
Specifications for Volume Migration..................................................................6-37
Commands to control Volume Migration........................................................... 6-39
Relations between "cc" command issues and status.......................................... 6-42
Restrictions for Volume Migration.....................................................................6-43
Universal Replicator MxN configuration and control..................................................6-44
Overview........................................................................................................6-44
Policy ............................................................................................................6-44
horcm.conf.....................................................................................................6-45
Command specifications.................................................................................. 6-46
pairdisplay command.............................................................................6-46
pairsplit command................................................................................. 6-47
Notice on system operation............................................................................. 6-50
Configuration examples...................................................................................6-52
Duplication of CCI applications...............................................................................6-54
Requirements for duplication of CCI................................................................. 6-57
Note for duplication of CCI.............................................................................. 6-58
Remote volume discovery......................................................................................6-58
Discovering a remote volume...........................................................................6-59
7 Data protection operations with CCI.......................................................7-1
Data protection operations...................................................................................... 7-2
Data Retention Utility .......................................................................................7-2
Restrictions on Data Retention Utility volumes...........................................7-3
Database Validator .......................................................................................... 7-3
Restrictions on Database Validator............................................................7-4
Protection parameters and operations...................................................................... 7-5
Data Protection facility............................................................................................ 7-5
Data Protection Facility specifications................................................................. 7-7
Examples for configuration and protected volumes..............................................7-8
Operation authority with CMD security enabled...................................................7-9
Target commands for protection........................................................................7-9
permission command...................................................................................... 7-10
New options for security..................................................................................7-10
raidscan -find inst..................................................................................7-10
raidscan -find verify [MU#].................................................................... 7-11
raidscan -f[d]........................................................................................ 7-11
pairdisplay -f[d].....................................................................................7-12
Permitting protected volumes.......................................................................... 7-12
With a $HORCMPERM file.......................................................................7-12
Without a $HORCMPERM file: Commands to run on different operating
systems................................................................................................ 7-13
Environment variables.....................................................................................7-14
$HORCMPROMOD................................................................................. 7-14
$HORCMPERM.......................................................................................7-15
Determining the protection mode command device........................................... 7-15
viii
Command Control Interface User and Reference Guide

8 Examples of using CCI commands .........................................................8-1
Group version control for mixed storage system configurations.................................. 8-2
LDM volume discovery and flushing for Windows...................................................... 8-2
Volume discovery function.................................................................................8-3
Mountvol attached to Windows 2012/2008/2003/2000 systems........................... 8-5
System buffer flushing function......................................................................... 8-6
Special facilities for Windows systems...................................................................... 8-9
Signature changing facility for Windows systems.................................................8-9
GPT disk for Windows..................................................................................... 8-10
Directory mount facility for Windows systems................................................... 8-12
Host group control................................................................................................ 8-14
Specifying a host group...................................................................................8-14
Commands and options including a host group................................................. 8-15
Using CCI SLPR security........................................................................................ 8-16
Specifying the SLPR Protection Facility............................................................. 8-17
SLPR configuration examples...........................................................................8-18
9 Troubleshooting....................................................................................9-1
General troubleshooting.......................................................................................... 9-2
Operational notes and restrictions for CCI operations................................................ 9-3
Error messages and error codes...............................................................................9-6
System log messages........................................................................................9-6
Command error messages ................................................................................9-8
Generic error codes (horctakeover and pair commands).................................... 9-18
Generic error codes (raidscan, raidqry, raidar, horcctl).......................................9-20
Specific error codes.........................................................................................9-21
SSB codes...................................................................................................... 9-22
SSB codes returned by the replication commands.................................... 9-22
SSB codes returned by the configuration setting command (raidcom)........9-24
Other SSB codes indicating internal errors............................................. 9-197
Calling Hitachi Data Systems customer support..................................................... 9-199
Index
ix
Command Control Interface User and Reference Guide

x
Command Control Interface User and Reference Guide

Preface
This document describes and provides instructions for using the Command
Control Interface (CCI) software to configure and perform operations on the
Hitachi RAID storage systems.
Please read this document carefully to understand how to use this product,
and maintain a copy for reference purposes.
□
Intended audience
□
Product version
□
Release notes
□
Changes in this revision
□
Referenced documents
□
Document conventions
□
Convention for storage capacity values
□
Accessing product documentation
□
Getting help
□
Comments
Preface
xi
Command Control Interface User and Reference Guide

Intended audience
This document is intended for system administrators, Hitachi Data Systems
representatives, and authorized service providers who install, configure, and
operate the Hitachi RAID storage systems.
Readers of this document should be familiar with the following:
• Data processing and RAID storage systems and their basic functions.
• The Hitachi RAID storage system and the manual for the storage system
(for example, Hardware Guide, Hitachi Virtual Storage Platform User and
Reference Guide).
• The management software for the storage system (for example, Hitachi
Command Suite, Hitachi Device Manager - Storage Navigator) and the
applicable user manuals (for example, Hitachi Command Suite User
Guide, System Administrator Guide, Hitachi Storage Navigator User
Guide).
• The host systems attached to the Hitachi RAID storage systems.
Product version
This document revision applies to Command Control Interface software
version 01-41-03/xx or later.
Release notes
The CCI release notes are available on Hitachi Data Systems Support
Connect:
https://knowledge.hds.com/Documents. Read the release notes
before installing and using this product. They may contain requirements or
restrictions that are not fully described in this document or updates or
corrections to this document.
Changes in this revision
• Added instructions for configuring iSCSI virtual ports (
Setting an iSCSI
virtual port on page 5-44, Deleting an iSCSI virtual port on page 5-44).
• Added information about the raidcom get quorum, raidcom modify
quorum, and raidcom replace quorum commands (
Commands executed
depending on operation authorities on page 3-13, Operation target for
raidcom commands when specifying the virtual storage machine in
HORCM_VCMD on page 3-61).
• Added information about creating external volumes using iSCSI (Creating
external volumes (iSCSI) on page 5-47).
• Added information about moving a parity group by specifying the LDEV
numbers of virtual volumes of Dynamic Provisioning, Copy-on-Write
Snapshot, or Thin Image (
Moving parity groups on page 5-54).
• Updated the error code tables.
xii
Preface
Command Control Interface User and Reference Guide

Referenced documents
Command Control Interface:
• Command Control Interface Installation and Configuration Guide,
MK-90RD7008
• Command Control Interface User and Reference Guide, MK-90RD7010
Hitachi Command Suite:
• Hitachi Command Suite User Guide, MK-90HC172
Hitachi Virtual Storage Platform G200, G400, G600, G800 and Hitachi Virtual
Storage Platform F400, F600, F800:
• Hitachi Thin Image User Guide, MK-92RD8011
• Product Overview for Hitachi Virtual Storage Platform Gx00 and Fx00
Models, MK-94HM8013
• Provisioning Guide for Hitachi Virtual Storage Platform Gx00 and Fx00
Models, MK-94HM8014
• System Administrator Guide, MK-94HM8016
• Hitachi Device Manager - Storage Navigator Messages, MK-94HM8017
• Hitachi TrueCopy® User Guide, MK-94HM8019
• Hitachi ShadowImage® User Guide, MK-94HM8021
• Hitachi Universal Replicator User Guide, MK-94HM8023
• Hitachi Universal Volume Manager User Guide, MK-92RD8024
• Global-Active Device User Guide, MK-92RD8072
Hitachi Virtual Storage Platform G1000, G1500, and Hitachi Virtual Storage
Platform F1500:
• Hitachi Thin Image User Guide, MK-92RD8011
• Provisioning Guide for Open Systems, MK-92RD8014
• System Administrator Guide, MK-92RD8016
• Hitachi Device Manager - Storage Navigator Messages, MK-92RD8017
• Hitachi TrueCopy® User Guide, MK-92RD8019
• Hitachi ShadowImage® User Guide, MK-92RD8021
• Hitachi Universal Replicator User Guide, MK-92RD8023
• Hitachi Universal Volume Manager User Guide, MK-92RD8024
• Product Overview, MK-92RD8051
• Global-Active Device User Guide, MK-92RD8072
Hitachi Unified Storage VM:
• Hitachi Unified Storage VM Block Module Provisioning Guide,
MK-92HM7012
• Hitachi ShadowImage® User Guide, MK-92HM7013
• Hitachi Storage Navigator User Guide, MK-92HM7016
Preface
xiii
Command Control Interface User and Reference Guide

• Hitachi Storage Navigator Messages, MK-92HM7017
• Hitachi TrueCopy® User Guide, MK-92HM7018
• Hitachi Universal Replicator User Guide, MK-92HM7019
• Hitachi Universal Volume Manager User Guide, MK-92HM7020
Hitachi Virtual Storage Platform:
• Hitachi Copy-on-Write Snapshot User Guide, MK-90RD7013
• Provisioning Guide for Mainframe Systems, MK-90RD7021
• Provisioning Guide for Open Systems, MK-90RD7022
• Hitachi ShadowImage® for Mainframe User Guide, MK-90RD7023
• Hitachi ShadowImage® User Guide, MK-90RD7024
• Hitachi Storage Navigator User Guide, MK-90RD7027
• Hitachi Storage Navigator Messages, MK-90RD7028
• Hitachi TrueCopy® User Guide, MK-90RD7029
• Hitachi TrueCopy® for Mainframe User Guide, MK-90RD7030
• Hitachi Universal Replicator for Mainframe User Guide, MK-90RD7031
• Hitachi Universal Replicator User Guide, MK-90RD7032
• Hitachi Universal Volume Manager User Guide, MK-90RD7033
• Hitachi Thin Image User Guide, MK-90RD7179
Hitachi Universal Storage Platform V/VM:
• Hitachi Copy-on-Write Snapshot User Guide, MK-96RD607
• LUN Manager User’s Guide, MK-96RD615
• Hitachi ShadowImage® for Mainframe User Guide, MK-96RD619
• Hitachi ShadowImage® User Guide, MK-96RD618
• Hitachi Storage Navigator User Guide, MK-96RD621
• Hitachi Storage Navigator Messages, MK-96RD613
• Hitachi TrueCopy® User Guide, MK-96RD622
• Hitachi TrueCopy® for Mainframe User Guide, MK-96RD623
• Hitachi Universal Replicator for Mainframe User Guide, MK-96RD625
• Hitachi Universal Replicator User Guide, MK-96RD624
• Hitachi Universal Volume Manager User Guide, MK-96RD626
Document conventions
This document uses the following terminology conventions:
Convention Description
Hitachi RAID
storage system
Refers to all supported storage system models, unless otherwise
noted.
xiv
Preface
Command Control Interface User and Reference Guide

Convention Description
Hitachi Virtual
Storage Platform
G200, G400, G600,
G800 (VSP G200,
G400, G600, G800)
VSP Gx00 models
Refers to all models of the Hitachi Virtual Storage Platform G200,
G400, G600, G800 storage systems, unless otherwise noted.
Hitachi Virtual
Storage Platform
F400, F600, F800
(VSP F400, F600,
F800)
VSP Fx00 models
VSP F series
Refers to all models of the Hitachi Virtual Storage Platform F400,
F600, F800 storage systems, unless otherwise noted.
Hitachi enterprise
storage system
Refers to the Hitachi RAID storage systems except for the VSP
Gx00 models, VSP Fx00 models, and HUS VM.
This document uses the following typographic conventions:
Convention Description
Bold • Indicates text in a window, including window titles, menus,
menu options, buttons, fields, and labels. Example: Click OK.
• Indicates emphasized words in list items.
Italic • Indicates a document title or emphasized words in text.
• Indicates a variable, which is a placeholder for actual text
provided by the user or for output by the system. Example:
pairdisplay -g group
(For exceptions to this convention for variables, see the
entry for angle brackets.)
Monospace
Indicates text that is displayed on screen or entered by the user.
Example: pairdisplay -g oradb
< > (angle brackets) Indicates variables in the following scenarios:
• Variables are not clearly separated from the surrounding text
or from other variables. Example:
Status-<report-name><file-version>.csv
• Variables in headings.
[ ] (square brackets) Indicates optional values. Example: [ a | b ] indicates that you
can choose a, b, or nothing.
{ } (braces) Indicates required or expected values. Example: { a | b }
indicates that you must choose either a or b.
| (vertical bar) Indicates that you have a choice between two or more options or
arguments. Examples:
[ a | b ] indicates that you can choose a, b, or nothing.
{ a | b } indicates that you must choose either a or b.
↓value↓ floor Floor function (round down value to the next integer)
Preface
xv
Command Control Interface User and Reference Guide

Convention Description
floor(value)
↑value↑ ceiling
ceiling(value)
Ceiling function (round up value to the next integer)
_ (underlined text) Default value
This document uses the following icons to draw attention to information:
Icon Label Description
Note Calls attention to important or additional information.
Tip Provides helpful information, guidelines, or suggestions for
performing tasks more effectively.
Caution Warns the user of adverse conditions or consequences (for
example, disruptive operations).
WARNING Warns the user of severe conditions or consequences (for
example, destructive operations).
Convention for storage capacity values
Physical storage capacity values (for example, disk drive capacity) are
calculated based on the following values:
Physical capacity unit Value
1 KB
1,000 (10
3
) bytes
1 MB
1,000 KB or 1,000
2
bytes
1 GB
1,000 MB or 1,000
3
bytes
1 TB
1,000 GB or 1,000
4
bytes
1 PB
1,000 TB or 1,000
5
bytes
1 EB
1,000 PB or 1,000
6
bytes
Logical storage capacity values (for example, logical device capacity) are
calculated based on the following values:
Logical capacity unit Value
1 block 512 bytes
1 cylinder Mainframe: 870 KB
Open-systems:
• OPEN-V: 960 KB
xvi
Preface
Command Control Interface User and Reference Guide

Logical capacity unit Value
• Others: 720 KB
1 KB
1,024 (2
10
) bytes
1 MB
1,024 KB or 1,024
2
bytes
1 GB
1,024 MB or 1,024
3
bytes
1 TB
1,024 GB or 1,024
4
bytes
1 PB
1,024 TB or 1,024
5
bytes
1 EB
1,024 PB or 1,024
6
bytes
Accessing product documentation
Product documentation is available on Hitachi Data Systems Support
Connect:
https://knowledge.hds.com/Documents. Check this site for the
most current documentation, including important updates that may have
been made after the release of the product.
Getting help
Hitachi Data Systems Support Connect is the destination for technical
support of products and solutions sold by Hitachi Data Systems. To contact
technical support, log on to Hitachi Data Systems Support Connect for
contact information: https://support.hds.com/en_us/contact-us.html.
Hitachi Data Systems Community is a new global online community for
HDS customers, partners, independent software vendors, employees, and
prospects. It is the destination to get answers, discover insights, and make
connections. Join the conversation today! Go to community.hds.com,
register, and complete your profile.
Comments
Please send us your comments on this document: [email protected].
Include the document title and number, including the revision level (for
example, -07), and refer to specific sections and paragraphs whenever
possible. All comments become the property of Hitachi Data Systems
Corporation.
Thank you!
Preface
xvii
Command Control Interface User and Reference Guide

xviii
Preface
Command Control Interface User and Reference Guide

1
Overview
This chapter provides an overview of the Command Control Interface (CCI)
software and CCI operations on the Hitachi RAID storage systems.
□
About Command Control Interface
□
CCI functions
□
CCI functions available on all RAID storage systems
Overview
1-1
Command Control Interface User and Reference Guide

About Command Control Interface
The Command Control Interface software enables you to perform storage
system configuration and data management operations by issuing commands
to the Hitachi RAID storage systems:
• Hitachi Virtual Storage Platform G200, G400, G600, G800
• Hitachi Virtual Storage Platform F400, F600, F800
• Hitachi Virtual Storage Platform G1000 and G1500 (VSP G1000 and
G1500)
For information about availability of Virtual Storage Platform F1500,
contact your Hitachi Data Systems representative.
• Hitachi Virtual Storage Platform F1500 (VSP F1500)
• Hitachi Unified Storage VM (HUS VM)
• Hitachi Virtual Storage Platform (VSP)
• Hitachi Universal Storage Platform V/VM (USP V/VM)
• Hitachi TagmaStore® Universal Storage Platform (TagmaStore USP)
• Hitachi TagmaStore® Network Storage Controller (TagmaStore NSC)
CCI continues to provide the proven functionality that has been available for
the USP V/VM and previous storage system models, including in-system
replication, remote replication, and data protection operations.
In addition, CCI for VSP and later provides command-line access to the same
provisioning and storage management operations that are available in the
GUI software (for example, Hitachi Command Suite, Storage Navigator). CCI
commands can be used interactively or in scripts to automate and
standardize storage administration functions, thereby simplifying the job of
the storage administrator and reducing administration costs.
Note: If a storage system rejects CCI commands, verify the software licenses
for the storage system (for example, TrueCopy) and the status of the
software product and storage system.
CCI functions
CCI functions matrix
The following table lists and describes the CCI functions available on the
Hitachi storage systems.
1-2
Overview
Command Control Interface User and Reference Guide
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
Page is loading ...
-
 1
1
-
 2
2
-
 3
3
-
 4
4
-
 5
5
-
 6
6
-
 7
7
-
 8
8
-
 9
9
-
 10
10
-
 11
11
-
 12
12
-
 13
13
-
 14
14
-
 15
15
-
 16
16
-
 17
17
-
 18
18
-
 19
19
-
 20
20
-
 21
21
-
 22
22
-
 23
23
-
 24
24
-
 25
25
-
 26
26
-
 27
27
-
 28
28
-
 29
29
-
 30
30
-
 31
31
-
 32
32
-
 33
33
-
 34
34
-
 35
35
-
 36
36
-
 37
37
-
 38
38
-
 39
39
-
 40
40
-
 41
41
-
 42
42
-
 43
43
-
 44
44
-
 45
45
-
 46
46
-
 47
47
-
 48
48
-
 49
49
-
 50
50
-
 51
51
-
 52
52
-
 53
53
-
 54
54
-
 55
55
-
 56
56
-
 57
57
-
 58
58
-
 59
59
-
 60
60
-
 61
61
-
 62
62
-
 63
63
-
 64
64
-
 65
65
-
 66
66
-
 67
67
-
 68
68
-
 69
69
-
 70
70
-
 71
71
-
 72
72
-
 73
73
-
 74
74
-
 75
75
-
 76
76
-
 77
77
-
 78
78
-
 79
79
-
 80
80
-
 81
81
-
 82
82
-
 83
83
-
 84
84
-
 85
85
-
 86
86
-
 87
87
-
 88
88
-
 89
89
-
 90
90
-
 91
91
-
 92
92
-
 93
93
-
 94
94
-
 95
95
-
 96
96
-
 97
97
-
 98
98
-
 99
99
-
 100
100
-
 101
101
-
 102
102
-
 103
103
-
 104
104
-
 105
105
-
 106
106
-
 107
107
-
 108
108
-
 109
109
-
 110
110
-
 111
111
-
 112
112
-
 113
113
-
 114
114
-
 115
115
-
 116
116
-
 117
117
-
 118
118
-
 119
119
-
 120
120
-
 121
121
-
 122
122
-
 123
123
-
 124
124
-
 125
125
-
 126
126
-
 127
127
-
 128
128
-
 129
129
-
 130
130
-
 131
131
-
 132
132
-
 133
133
-
 134
134
-
 135
135
-
 136
136
-
 137
137
-
 138
138
-
 139
139
-
 140
140
-
 141
141
-
 142
142
-
 143
143
-
 144
144
-
 145
145
-
 146
146
-
 147
147
-
 148
148
-
 149
149
-
 150
150
-
 151
151
-
 152
152
-
 153
153
-
 154
154
-
 155
155
-
 156
156
-
 157
157
-
 158
158
-
 159
159
-
 160
160
-
 161
161
-
 162
162
-
 163
163
-
 164
164
-
 165
165
-
 166
166
-
 167
167
-
 168
168
-
 169
169
-
 170
170
-
 171
171
-
 172
172
-
 173
173
-
 174
174
-
 175
175
-
 176
176
-
 177
177
-
 178
178
-
 179
179
-
 180
180
-
 181
181
-
 182
182
-
 183
183
-
 184
184
-
 185
185
-
 186
186
-
 187
187
-
 188
188
-
 189
189
-
 190
190
-
 191
191
-
 192
192
-
 193
193
-
 194
194
-
 195
195
-
 196
196
-
 197
197
-
 198
198
-
 199
199
-
 200
200
-
 201
201
-
 202
202
-
 203
203
-
 204
204
-
 205
205
-
 206
206
-
 207
207
-
 208
208
-
 209
209
-
 210
210
-
 211
211
-
 212
212
-
 213
213
-
 214
214
-
 215
215
-
 216
216
-
 217
217
-
 218
218
-
 219
219
-
 220
220
-
 221
221
-
 222
222
-
 223
223
-
 224
224
-
 225
225
-
 226
226
-
 227
227
-
 228
228
-
 229
229
-
 230
230
-
 231
231
-
 232
232
-
 233
233
-
 234
234
-
 235
235
-
 236
236
-
 237
237
-
 238
238
-
 239
239
-
 240
240
-
 241
241
-
 242
242
-
 243
243
-
 244
244
-
 245
245
-
 246
246
-
 247
247
-
 248
248
-
 249
249
-
 250
250
-
 251
251
-
 252
252
-
 253
253
-
 254
254
-
 255
255
-
 256
256
-
 257
257
-
 258
258
-
 259
259
-
 260
260
-
 261
261
-
 262
262
-
 263
263
-
 264
264
-
 265
265
-
 266
266
-
 267
267
-
 268
268
-
 269
269
-
 270
270
-
 271
271
-
 272
272
-
 273
273
-
 274
274
-
 275
275
-
 276
276
-
 277
277
-
 278
278
-
 279
279
-
 280
280
-
 281
281
-
 282
282
-
 283
283
-
 284
284
-
 285
285
-
 286
286
-
 287
287
-
 288
288
-
 289
289
-
 290
290
-
 291
291
-
 292
292
-
 293
293
-
 294
294
-
 295
295
-
 296
296
-
 297
297
-
 298
298
-
 299
299
-
 300
300
-
 301
301
-
 302
302
-
 303
303
-
 304
304
-
 305
305
-
 306
306
-
 307
307
-
 308
308
-
 309
309
-
 310
310
-
 311
311
-
 312
312
-
 313
313
-
 314
314
-
 315
315
-
 316
316
-
 317
317
-
 318
318
-
 319
319
-
 320
320
-
 321
321
-
 322
322
-
 323
323
-
 324
324
-
 325
325
-
 326
326
-
 327
327
-
 328
328
-
 329
329
-
 330
330
-
 331
331
-
 332
332
-
 333
333
-
 334
334
-
 335
335
-
 336
336
-
 337
337
-
 338
338
-
 339
339
-
 340
340
-
 341
341
-
 342
342
-
 343
343
-
 344
344
-
 345
345
-
 346
346
-
 347
347
-
 348
348
-
 349
349
-
 350
350
-
 351
351
-
 352
352
-
 353
353
-
 354
354
-
 355
355
-
 356
356
-
 357
357
-
 358
358
-
 359
359
-
 360
360
-
 361
361
-
 362
362
-
 363
363
-
 364
364
-
 365
365
-
 366
366
-
 367
367
-
 368
368
-
 369
369
-
 370
370
-
 371
371
-
 372
372
-
 373
373
-
 374
374
-
 375
375
-
 376
376
-
 377
377
-
 378
378
-
 379
379
-
 380
380
-
 381
381
-
 382
382
-
 383
383
-
 384
384
-
 385
385
-
 386
386
-
 387
387
-
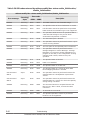 388
388
-
 389
389
-
 390
390
-
 391
391
-
 392
392
-
 393
393
-
 394
394
-
 395
395
-
 396
396
-
 397
397
-
 398
398
-
 399
399
-
 400
400
-
 401
401
-
 402
402
-
 403
403
-
 404
404
-
 405
405
-
 406
406
-
 407
407
-
 408
408
-
 409
409
-
 410
410
-
 411
411
-
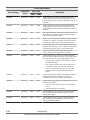 412
412
-
 413
413
-
 414
414
-
 415
415
-
 416
416
-
 417
417
-
 418
418
-
 419
419
-
 420
420
-
 421
421
-
 422
422
-
 423
423
-
 424
424
-
 425
425
-
 426
426
-
 427
427
-
 428
428
-
 429
429
-
 430
430
-
 431
431
-
 432
432
-
 433
433
-
 434
434
-
 435
435
-
 436
436
-
 437
437
-
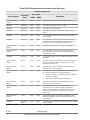 438
438
-
 439
439
-
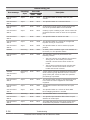 440
440
-
 441
441
-
 442
442
-
 443
443
-
 444
444
-
 445
445
-
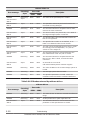 446
446
-
 447
447
-
 448
448
-
 449
449
-
 450
450
-
 451
451
-
 452
452
-
 453
453
-
 454
454
-
 455
455
-
 456
456
-
 457
457
-
 458
458
-
 459
459
-
 460
460
-
 461
461
-
 462
462
-
 463
463
-
 464
464
-
 465
465
-
 466
466
-
 467
467
-
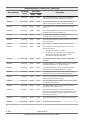 468
468
-
 469
469
-
 470
470
-
 471
471
-
 472
472
-
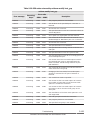 473
473
-
 474
474
-
 475
475
-
 476
476
-
 477
477
-
 478
478
-
 479
479
-
 480
480
-
 481
481
-
 482
482
-
 483
483
-
 484
484
-
 485
485
-
 486
486
-
 487
487
-
 488
488
-
 489
489
-
 490
490
-
 491
491
-
 492
492
-
 493
493
-
 494
494
-
 495
495
-
 496
496
-
 497
497
-
 498
498
-
 499
499
-
 500
500
-
 501
501
-
 502
502
-
 503
503
-
 504
504
-
 505
505
-
 506
506
-
 507
507
-
 508
508
-
 509
509
-
 510
510
-
 511
511
-
 512
512
-
 513
513
-
 514
514
-
 515
515
-
 516
516
-
 517
517
-
 518
518
-
 519
519
-
 520
520
-
 521
521
-
 522
522
-
 523
523
-
 524
524
-
 525
525
-
 526
526
-
 527
527
-
 528
528
-
 529
529
-
 530
530
Hitachi VSP G1500 User And Reference Manual
- Type
- User And Reference Manual
Ask a question and I''ll find the answer in the document
Finding information in a document is now easier with AI
Related papers
-
Hitachi VSP F600 User manual
-
Hitachi MK-90RD011-25 User manual
-
Hitachi Virtual Storage Platform G600 User manual
-
Hitachi G1000 User manual
-
Hitachi VSP F600 System Administration Manual
-
Hitachi G1500 User manual
-
Hitachi AMS 2000 Series User manual
-
Hitachi Universal Storage Platform V User manual
-
Hitachi Universal Storage Platform V User manual
-
Hitachi VSP F600 System Administrator Manual

















































































































































































































































































































































































































































































































































