Avaya BCM50, a feature-rich business communications system, empowers your company with exceptional voice, video, data and mobility solutions. Unify communications across diverse devices, including desk phones, softphones, video conferencing systems and mobile devices, enabling seamless collaboration and efficient operations. This scalable solution also integrates with leading business applications, enhancing productivity and streamlining workflows.
Avaya BCM50, a feature-rich business communications system, empowers your company with exceptional voice, video, data and mobility solutions. Unify communications across diverse devices, including desk phones, softphones, video conferencing systems and mobile devices, enabling seamless collaboration and efficient operations. This scalable solution also integrates with leading business applications, enhancing productivity and streamlining workflows.




















-
 1
1
-
 2
2
-
 3
3
-
 4
4
-
 5
5
-
 6
6
-
 7
7
-
 8
8
-
 9
9
-
 10
10
-
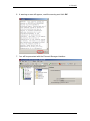 11
11
-
 12
12
-
 13
13
-
 14
14
-
 15
15
-
 16
16
-
 17
17
-
 18
18
-
 19
19
-
 20
20
-
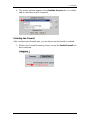 21
21
-
 22
22
-
 23
23
-
 24
24
-
 25
25
-
 26
26
Avaya BCM50, a feature-rich business communications system, empowers your company with exceptional voice, video, data and mobility solutions. Unify communications across diverse devices, including desk phones, softphones, video conferencing systems and mobile devices, enabling seamless collaboration and efficient operations. This scalable solution also integrates with leading business applications, enhancing productivity and streamlining workflows.
Ask a question and I''ll find the answer in the document
Finding information in a document is now easier with AI
Related papers
-
Avaya BCM50 User manual
-
Avaya BCM50 User manual
-
Avaya LAN CTE BCM Rls 6.0 User manual
-
Avaya BCM50 User manual
-
Avaya Personal Call Manager BCM Rls 6.0 User manual
-
Avaya Business Element Manager BCM Rls 6.0 User manual
-
Avaya Desktop Assistant Pro Admin Edition BCM Rls 6.0 User manual
-
Avaya Application Launcher BCM Rls 6.0 User manual
-
Avaya Alarm Manager BCM Rls 6.0 User manual
-
Avaya BCM50 User manual

























